Understanding how identity theft happens can make a big difference in how you choose to safeguard your personally identifiable information (PII). Here are 12 ways your personal information can land in the wrong hands, including tips to help protect your info against potential identity thieves.
1. Weak data protection
Weak data protection means failing to secure your personal information adequately, which can allow hackers to access your data and commit identity theft. This can result in unauthorized transactions, credit score damage, and financial losses. For example, if you use simple, easy-to-guess passwords, cybercriminals could break into your accounts, steal your identity, and make unauthorized purchases in your name.
Tips:
- Use strong, unique passwords for each account.
- Enable two-factor authentication on your accounts.
- Regularly update your software and devices to protect against security vulnerabilities.
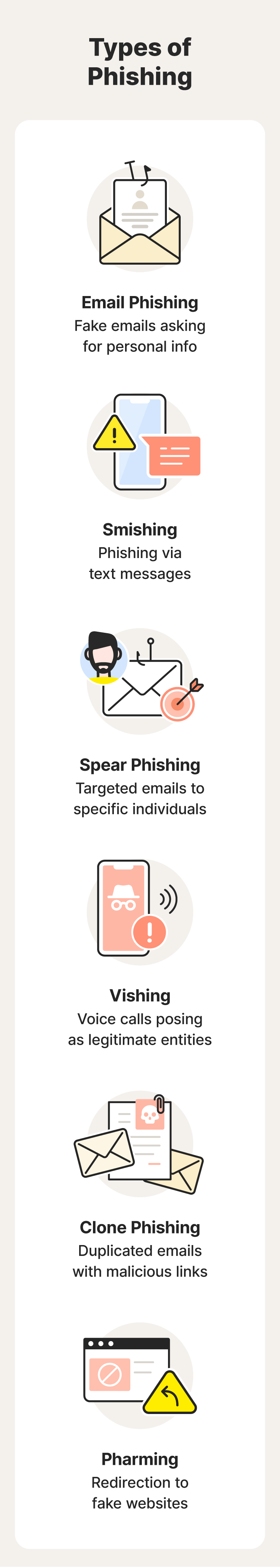
2. Phishing
Phishing occurs when scammers try to trick you into revealing sensitive information, such as your passwords or credit card numbers, by posing as an apparently trustworthy entity through emails, text messages, or fake websites. For example, you might receive an email supposedly from your bank asking you to click a link to update your account information. But when you click, you’re taken to a fraudulent website designed to steal your login credentials.
Tips:
- Verify a sender's legitimacy before clicking links in emails or texts.
- Manually type a URL into your browser instead of clicking links in emails to verify that messages come from legitimate companies.
- Remember that identity thieves often create fraudulent emails that appear genuine to deceive recipients.
3. Data breaches
A data breach is when unauthorized individuals access sensitive information, such as personal or financial data, stored by an organization. This can happen incidentally through a lost device or intentionally through hacking. The consequences of a data breach can be severe for both the organization and affected individuals.
Tips:
- Use breach detection tools.
- Use strong, unique passwords.
- Enable two-factor authentication.
- Update software and apps regularly.
- Be cautious of suspicious emails and links.
4. Unsafe internet connections
Unsafe internet connections, like public Wi-Fi, can allow cybercriminals to intercept data transmitted to and from your device and steal sensitive information. For example, a hacker might capture your login credentials if you log into your bank account over an unsecured public Wi-Fi network. Using a VPN encrypts your data during transmission, better protecting your personal information online and making it harder for hackers to intercept and steal the data you send and receive.
Tips:
- Avoid accessing sensitive information or making transactions over public Wi-Fi networks.
- Use a VPN to encrypt your internet connection and keep your browsing activity more private.
5. Mail theft
Mail theft is when someone steals your physical mail, often to obtain personal information. This can lead to identity theft if a fraudster uses that information to open accounts, make purchases, or commit fraud in your name. For example, someone who steals your credit card statement could use it to try to obtain your card number to make unauthorized charges.
Tips:
- Use a locked mailbox or a P.O. Box to secure your incoming mail.
- Opt for digital statements and bills whenever possible to limit the paper mail you receive.
6. Dumpster diving
Dumpster diving is when someone searches through your trash to find personal information like bank statements, credit card offers, or medical records. This method is surprisingly effective because people often discard without properly destroying documents containing sensitive information that scammers can then use to steal your identity.
The consequences of identity theft from dumpster diving can be severe. Thieves can open new credit accounts in your name, drain your bank accounts, or use your information to commit other forms of fraud. This can damage your credit score, result in unauthorized account charges, and lead to a long and complicated process to restore your identity.
Tips:
- Shred documents containing personal information before disposing of them.
- Lock your trash bins to prevent unauthorized access to discarded documents.
7. Lost Social Security card
A lost Social Security card can lead to identity theft if someone finds it and uses your Social Security number to open credit accounts, take out loans, or commit other fraud in your name. For example, a thief could use your SSN to apply for a credit card, leaving you on the hook for unauthorized purchases.
Tips:
- Don’t carry your Social Security card with you—keep it in a safe place in your home or a lock box.
- Report a lost Social Security card immediately to the Social Security Administration and the Federal Trade Commission.
- Place a fraud alert or credit freeze on your credit file to help prevent new accounts from being opened in your name.
8. Wallet theft
Wallets typically contain a trove of personal information and documents like credit cards, ID cards, and driver’s licenses. If your wallet is lost or stolen, a thief might be able to use your information and documentation to open accounts, make unauthorized purchases, or commit fraud—all of which could potentially harm your credit score.
Tips:
- Carry only essential items in your wallet and leave unnecessary documents at home.
- Keep a record of the contents and information in your wallet, including card numbers and contact information, so you can quickly report stolen cards.
- Immediately report lost or stolen cards to your bank.
9. Medical identity theft
Medical identity theft occurs when someone uses your personal information, like your health insurance number or medical records, to obtain medical services, prescription drugs, or to file false insurance claims. This type of theft can be particularly damaging because it can affect your finances, health insurance, and medical history.
The impacts of medical identity theft can be severe. You may find false entries in your medical records, leading to incorrect treatments or misdiagnoses. Additionally, your insurance could be billed for services you never received, resulting in higher premiums or out-of-pocket costs.
Tips:
- Securely store health insurance cards and medical records.
- Share health information only with trusted healthcare providers and organizations.
- Regularly review medical statements and insurance claims for unfamiliar services.
- Report any discrepancies immediately to your insurance company and healthcare provider.
10. Synthetic identity theft
Synthetic identity theft is a complex form of fraud in which criminals create a new identity using both real and fake information. For example, they may use a real Social Security number with a fake name and birthdate.
By creating a fake identity, criminals can open credit accounts, take out loans, and make large purchases without immediate suspicion. These synthetic identities often go unnoticed for a long time, allowing the criminals to build up significant debt in the victim's name.
Tips:
- Proactively place a credit lock or credit freeze with the credit bureaus to help prevent criminals from opening new accounts in your name.
- Safeguard your Social Security number and personal information; share them only when necessary and only with trusted entities.
11. Tax identity theft
Tax identity theft happens when someone uses your Social Security number to file a fraudulent tax return and claim a refund. If successful, a thief may deposit these refunds into accounts they control or distribute the money via prepaid debit cards, giving them direct access to the funds.
Victims of tax identity theft may experience delays in receiving legitimate tax refunds and potential tax liabilities resulting from fraudulent activity, which is why it’s so important to try to protect yourself against tax fraud.
Tips:
- File your tax return early to minimize the risk of fraudulent filings in your name.
- Be cautious of IRS phishing scams and don’t provide personal information over the phone or email unless you initiate contact.
- If you suspect tax identity theft, promptly report it to the IRS and file a Form 14039 Identity Theft Affidavit.
12. Child identity theft
Child identity theft occurs when someone—potentially even a parent or guardian—uses a minor's personal information, such as their Social Security number, to open fraudulent accounts or obtain loans. Child identity theft can go undetected for years, because a child's credit report is often not checked until they're older.
This delay can make it easier for criminals to use a child’s stolen identity for various fraudulent activities, including applying for credit cards, loans, or government benefits. As a result, the child’s credit history and financial standing may be hurt before they even become aware of the theft.
Tips:
- Regularly monitor your child's personal information, including their Social Security number, for suspicious activity.
- Consider freezing your child's credit report to prevent unauthorized access.
- Review any pre-approved credit offers addressed to your child.
What to do if you think your identity has been stolen
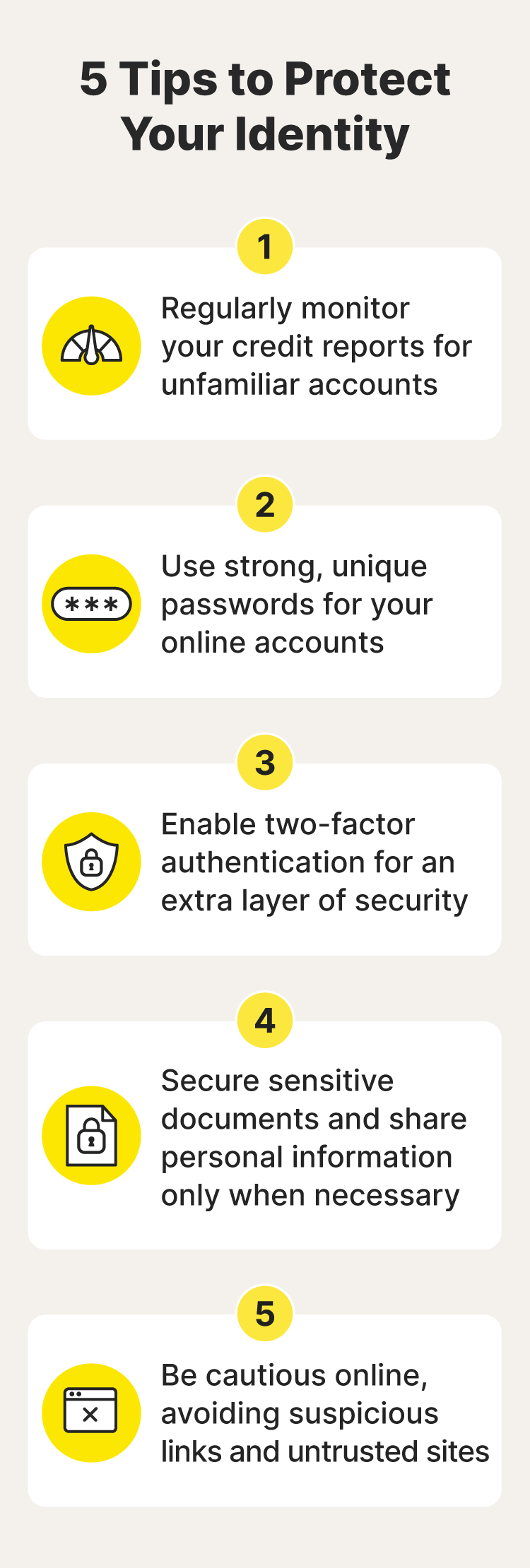
If you start to see signs of identity theft and suspect that somebody has access to your personal information, here's how to take action:
- Freeze your credit.
You’ll need to do this with each major credit bureau—Experian®, Equifax®, and TransUnion®. This precautionary measure restricts unauthorized access to your credit report and prevents new account openings.
- Inform financial institutions.
Report the ID theft and any potentially fraudulent activity to your bank, credit card companies, and other affected organizations. Contact their fraud department to close compromised accounts and request replacements.
- Report identity theft to the Federal Trade Commission (FTC).
Visit IdentityTheft.gov to file a report and initiate the recovery process.
- File a police report.
Report the ID theft to your local law enforcement agency, especially if you have proof. Your report can help others in your area avoid identity theft too.
- Notify relevant agencies.
Report stolen ID cards and driver’s licenses to the DMV, tell the IRS about compromised SSNs, and notify your health insurer about the identity theft incident. - Secure compromised accounts.
Immediately log out of potentially affected accounts, change compromised passwords, and enable two-factor authentication (2FA) and additional security measures wherever possible.
Following these steps will help you minimize the impact of identity theft and gird yourself against further fraudulent activity.
Experience unparalleled protection with LifeLock
Identity fraud can be devastating, impacting your finances, credit, and reputation. LifeLock is a powerful identity protection service with features like Privacy Monitor and Dark Web Monitoring that help reduce public exposure of your personal information.
LifeLock monitors for fraudulent use of your Social Security number and other personal details and alerts you in the event of potential misuse. Subscribe to LifeLock today to keep your sensitive information safer, help protect against identity fraud, and enjoy greater peace of mind.
We do not monitor all transactions at all businesses. No one can prevent all identity theft.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about.
This article contains
- 1. Weak data protection
- 2. Phishing
- 3. Data breaches
- 4. Unsafe internet connections
- 5. Mail theft
- 6. Dumpster diving
- 7. Lost Social Security card
- 8. Wallet theft
- 9. Medical identity theft
- 10. Synthetic identity theft
- 11. Tax identity theft
- 12. Child identity theft
- What to do if you think your identity has been stolen
- Experience unparalleled protection with LifeLock
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.




