What is the dark web?
The dark web is a part of the internet hidden from the general population that requires special software to access. Traffic on the dark web is practically untraceable, so it’s often used by those who want to remain anonymous online. Sometimes called the “darknet,” the dark web has millions of users worldwide but represents a very small share of the deep web, which some estimates say accounts for more than 99% of the internet.

What is the difference between the dark web and the deep web?
The deep web refers to any part of the internet that isn't indexed by search engines and requires login credentials like passwords to access. In contrast, the dark web is intentionally hidden and requires special software to access.
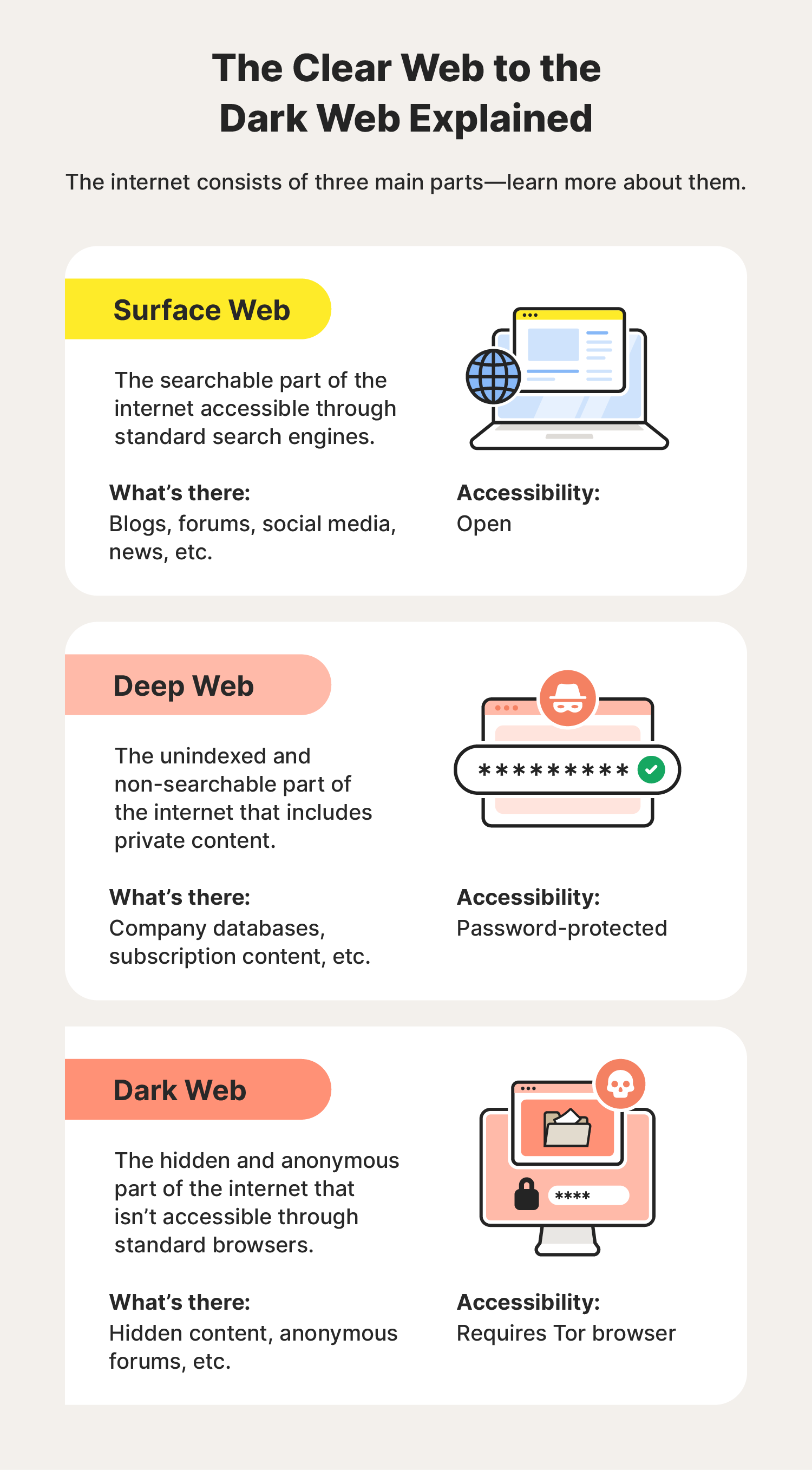
The internet consists of three main parts: the surface web, the deep web, and the dark web. Although some people use the terms “deep web” and “dark web” interchangeably, that’s a misnomer. Both are hidden from the general public online, but there are major differences in how each of them is accessed and used.
- Surface web: Sometimes called the clear web, the surface web is the part of the internet that most people see when they go online. Here, you can easily find information because search engines like Google index this content. That means that they crawl content published online, organize it, and make it searchable.
- Deep web: This is the part of the internet you can’t reach through traditional search engines. The deep web is where you go when you need to use login credentials to access accounts and bypass paywalls. Anytime you open your email account, make purchases online, access medical records, search through corporate databases, or access other sensitive or protected corners online, you’re in the deep web.
- Dark web: The dark web, or darknet, is a part of the deep web that’s intentionally hidden and accessible only with special software like the Tor browser. Political dissidents, whistleblowers, cybercriminals, and others who want to remain anonymous online can use the dark web to keep their activity essentially untraceable.
What is the dark web used for?
When most people think of the dark web, they think of crime. And yes, there is a hotbed of counterfeit money, stolen credit cards and login credentials, illegal pornography, trafficking, pirated movies, and prohibited drugs. But the dark web is also used by activists, journalists, political dissidents, and whistleblowers.
Here are some of the shady or illegal things people buy or sell on the dark web:
- Illegal drugs
- Weapons
- Cyber weapons
- Passwords
- Credit card information
- Stolen identities
- Pornography
- Harmful materials
In addition to nefarious or criminal activity, the dark web is also used for:
- Activism
- Anonymous browsing
- Journalism
- Private communication
- Whistleblowing
Law enforcement agencies also often use the dark web to identify, surveil, and shut down criminal operations. But even if you have good intentions on the dark web, the lack of guardrails means one misstep could expose you to malware, keyloggers, ransomware, or depraved content.
What happens if you go on the dark web?
The clear web and dark web are similar in many ways—once you open a browser, you can enter a URL and start browsing. The main difference is how you search, what you might see, and the possible consequences of using the platform.
If you visit dark web websites without knowing what you’re doing, you may experience the following:
- Legal consequences: Governments around the world are cracking down on dark web marketplaces and those who use them to buy and sell illegal goods and services.
- Malware infections: By clicking the wrong link or downloading a bad file, you can trigger a malware download that infects your device and steals information.
- Scams and fraud: Criminals tend to frequent the dark web, and if you aren’t careful, you might get scammed out of money or blackmailed.
- Data leaks: The dark web isn’t as private as you might think, and other users might leak your personally identifiable information after a data breach or steal your identity.
- Negative psychological impacts: Illegal and hard-to-stomach content is often published on the dark web since it’s an unregulated information highway.
How to access the dark web in 3 steps
Using the dark web is risky and you should always be extremely careful—even if you’re using it for legal and ethical reasons like secure messaging, security research, and cybersecurity training. If you do need to use the dark web, you can do it by following these three steps:
1. Access the Tor browser
TOR (The Onion Router) is a free and open-source web browser. It was built to prevent surveillance and censorship and is the gateway to the dark web. Launched in 2002, it encrypts sessions, hides users’ IP addresses and browsing activity, and re-routes web traffic through relay nodes, exit relays, and bridges.
2. Choose a dark web search engine
Next, you’ll have to choose a search engine that works on the dark web. Some popular options are surface web search engines that are compatible with the dark web; other dark web search engines work exclusively on Tor browser. Note that unlike on the surface web, dark web search engines act more like private browsing tools, because web pages on the dark web aren’t indexed and sorted.
3. Search for dark web websites
Websites look alike on the dark web and surface web. However, some differences make it more difficult to find what you’re looking for with a typical search on the darknet:
- Domain suffixes: Most sites you visit end in “.com” or “.org.” But on the dark web, they typically end in “.onion.”
- URLs: Surface websites usually make sense as part of a brand or business name. However, dark web URLs tend to have a random mix of characters.
If you’re looking for something specific, dark web users suggest looking up onion links on The Hidden Wiki or the r/TOR subreddit. Keep in mind that dark web directories often return 404 not found errors when websites and marketplaces get taken down.
What tools can help keep you safe on the deep dark web?
As mentioned above, accessing the dark web comes with risks. Thankfully, there are tools you can use to help protect against cyberthreats. Some of these tools include:
- VPNs: The Tor browser already scrambles traffic, but you can also use a separate VPN to help mask your sessions. This is called VPN over Tor.
- Encrypted messaging apps: Use secure messaging apps like Signal and Telegram to message others privately.
- PGP encryption: Encrypt and decrypt sensitive messages, files, and signatures with the Pretty Good Privacy security program.
- Updated devices: Make sure your device is running on the latest operating system to reduce your vulnerability to security exploits.
- LifeLock: Use an identity theft protection service for help with dark web monitoring, personal information exposure reduction, Social Security number alerts, and identity restoration.
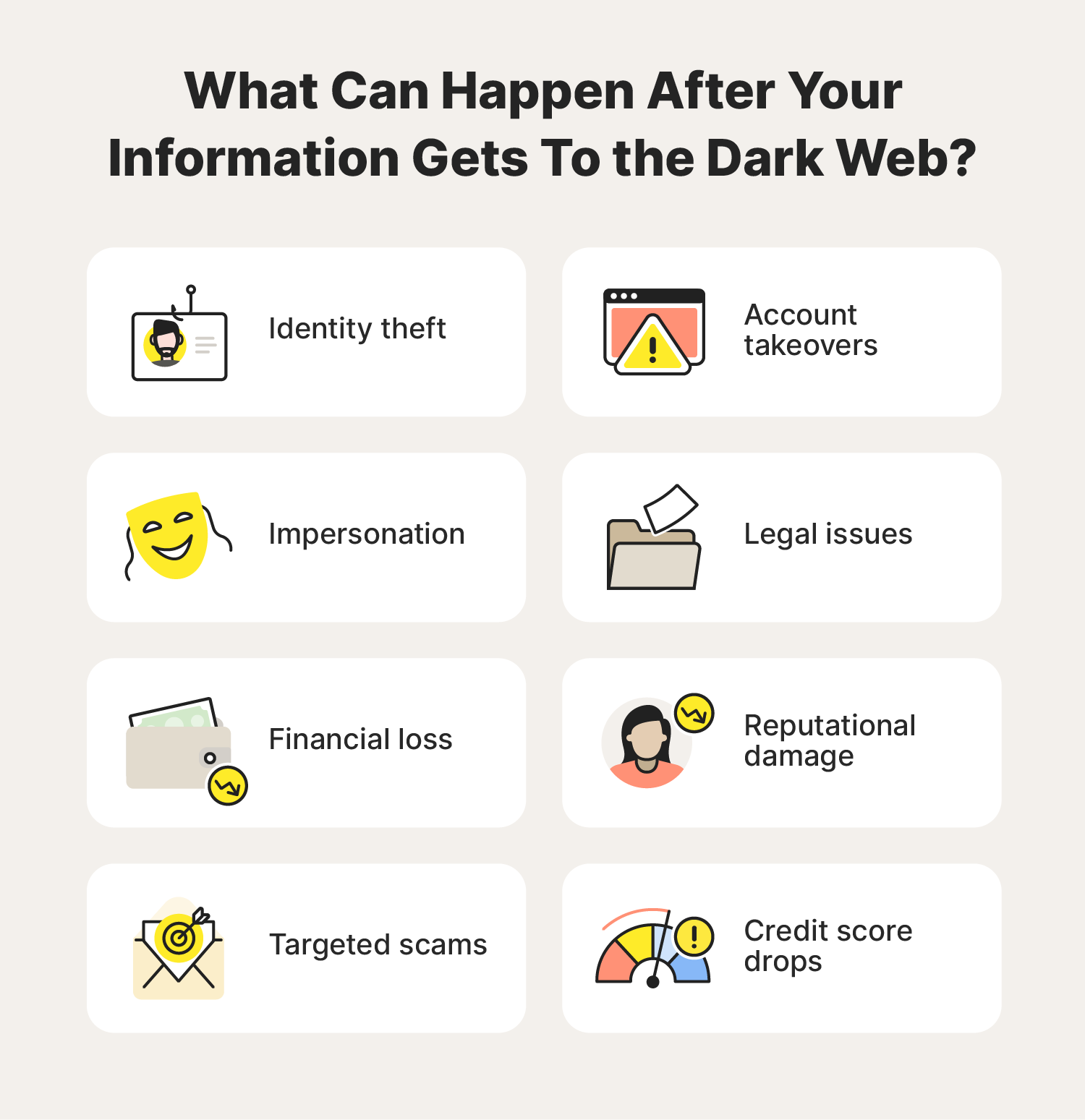
What happens if your information is on the dark web?
If somebody steals sensitive information like your Social Security number or bank account details, and leaks it on the dark web, several things can happen. For example, you might experience:
- Identity theft
- Impersonation
- Financial loss
- Targeted scams
- Account takeovers
- Legal issues
- Reputational damage
- Credit score drops
You can find out if somebody leaked your information by using an identity protection suite like LifeLock that includes a built-in dark web monitoring feature. If you discover your information was compromised, you should immediately report it and begin the identity theft recovery process.
How to recover if your information was leaked on the dark web
To start the dark web data leak recovery process, report the identity theft to local law enforcement and follow our guide on what to do if your identity is stolen. You may wish to consult a financial advisor to assist with the process. Here are a few specific steps to take depending on your situation.
- If your Social Security number was exposed: File a report with the FTC and freeze your credit.
- If you know the criminal or you need a police report: Report the crime to local law enforcement to get justice faster or obtain a copy of the police report for interested parties like creditors and insurance companies.
- If your financial accounts were compromised: Talk to your bank, credit card issuer, or loan lender to update your account login credentials and ensure the proper safeguards are in place to prevent unauthorized transactions.
- If your credit card number was stolen: Freeze your credit cards and associated bank accounts.
Safeguard against identity theft after data leaks
If your private information makes it to the dark web, you may have to combat identity theft and possibly stolen funds. There may even be a threat to your safety.
Identity theft protection services like LifeLock can help you take swift preventative action if your data is discovered on the dark web, and ensure you have protections in place to help recover from identity theft and fraud.
FAQs about the dark web
Still have questions about the dark web? Here’s what you need to know.
What is the government doing about the dark web?
In the U.S., the FBI is leading the charge to take down illicit websites and marketplaces. In 2013 and 2014, they successfully shut down the notorious Silk Road and the New Silk Road. The FBI is also making progress in de-anonymizing users by setting up nodes that work as relays, allowing agents to identify criminal activity.
What is the dark web browser?
The dark web browser is Tor, which stands for The Onion Router. Tor is specially designed to enable access to dark websites and anonymize traffic by passing it through several encrypted “layers” via a complex network of nodes and relays.
Can you be tracked on the dark web?
It’s possible but unlikely. Generally, only the government or someone with advanced technology and extensive resources can track you down. Even then, it’s extremely difficult and time-consuming. That said, most governments only use their resources to track down big players and don’t spend a lot of time looking for average users.
When is it illegal to use the dark web?
It’s legal to access the dark web in the U.S. However, anything that’s illegal on the surface web is also illegal on the dark web. For example, it’s against the law to buy or sell stolen identities, drugs, weapons, login credentials, or illicit pornography. It’s also illegal to participate in acts or discussions of terrorism.
Disclaimer: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about online threats. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime and LifeLock does not monitor or protect against all dangers on the dark web.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- What is the dark web?
- What is the dark web used for?
- What happens if you go on the dark web?
- How to access the dark web in 3 steps
- What tools can help keep you safe on the deep dark web?
- What happens if your information is on the dark web?
- How to recover if your information was leaked on the dark web
- Safeguard against identity theft after data leaks
- FAQs about the dark web
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.