If your PII is exposed, a cybercriminal could sell your information on the dark web, steal your identity, or rack up debts in your name. To help mitigate fallout from exposed PII, take precautions and learn how to recognize the most common ruses cybercriminals use to steal personally identifiable information.
Read on to learn more about PII and what it takes to keep it safe.
What is personally identifiable information (PII)?
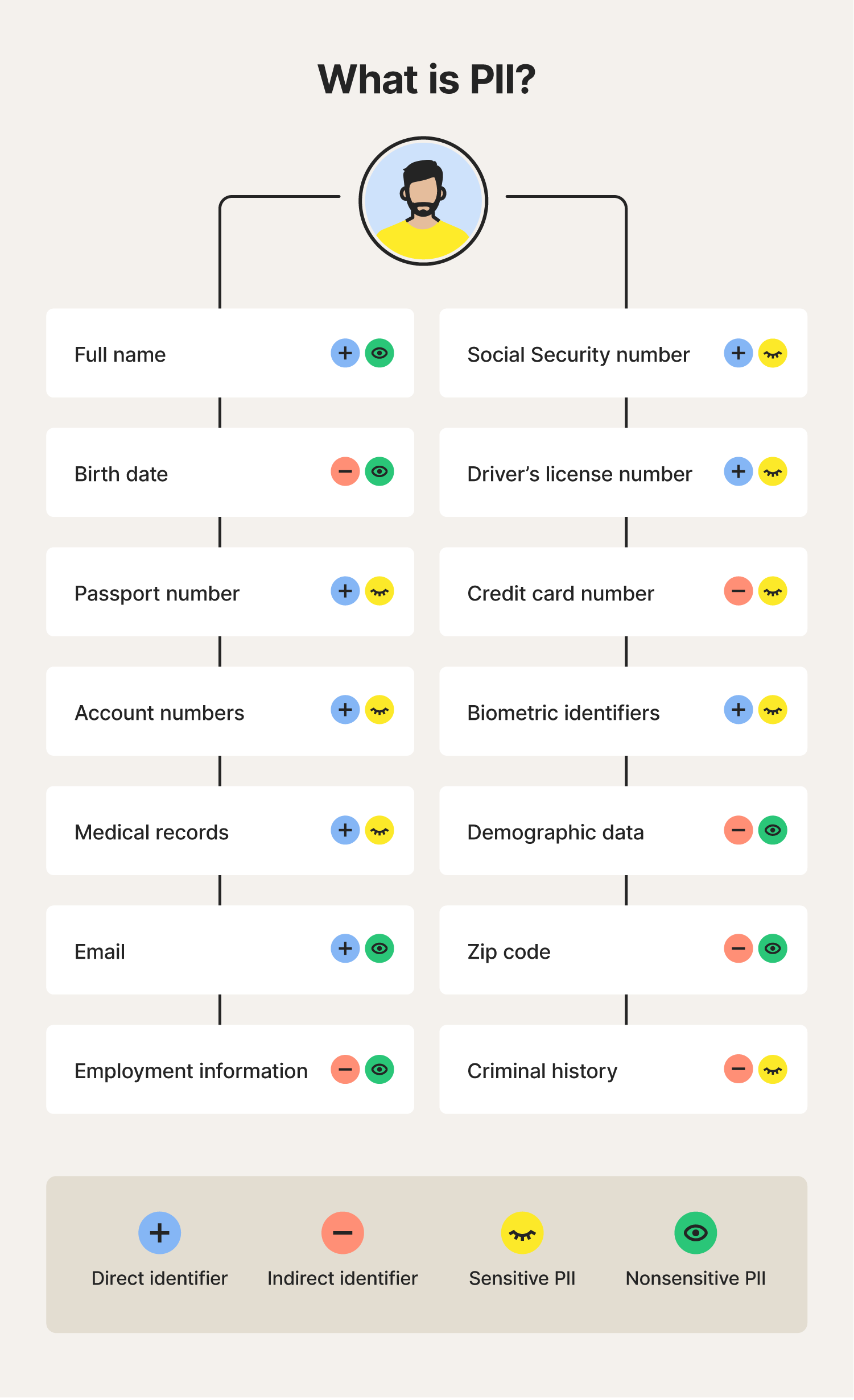
PII, or personally identifiable information, is any data that can identify a specific person. PII data can be sensitive or nonsensitive, depending on how easily it can be used to identify someone. It includes personal details like your name, demographics, Social Security number, or medical records.
Sensitive vs. nonsensitive PII
Sensitive PII is personal information that can uniquely identify an individual and poses a serious risk of harm or fraud if exposed. By contrast, nonsensitive PII is generally publicly available information that doesn’t represent a significant threat to the individual on its own if shared or exposed.
Examples of sensitive PII:
- Social Security number
- Driver’s license number
- Passport number
- Credit card number
- Account numbers
- Biometric, genetic, or medical records
Some types of personal data may not be sensitive on their own but can become sensitive, or be used to get sensitive PII, if combined with other data. This type of information is usually considered nonsensitive PII, but it can still contribute to misuse in certain contexts.
Examples of nonsensitive PII:
- Full name
- Race
- Gender
- Zip code
- Birth date
- Employment information
Regardless of whether certain information is officially classified as sensitive or not, aim to protect all of your personal data as much as possible. Even personal data that seems nonsensitive can be combined with other information to reveal a more detailed picture of who you are. Avoid sharing sensitive information online; if you have to, use a VPN to encrypt and protect it.
Examples of PII identifiers
PII identifiers refer to how easily certain pieces of personal information can be used to identify an individual. Some PII may be enough on its own to identify someone (direct identifier), while other types can only expose someone’s identity when combined with other data (indirect identifier).
For example, medical records are a type of sensitive PII that contain multiple PII identifiers: Social Security number (direct identifier), birth date (indirect identifier), and full name (direct identifier).
Examples of direct identifiers:
- Name
- Biometric data (fingerprint, face ID)
- Social Security number
- Driver’s license number
Examples of indirect or quasi-identifiers:
- Birth date
- Zip code
- Demographic data
- Occupation
- Geolocation data
PHI vs. PII
Protected health information (PHI) is a specific type of PII that’s protected by the Health Insurance Portability and Accountability Act (HIPAA). PHI is any personal information in medical records that could be used to identify an individual and relates to their health, healthcare services, or healthcare payments.
Some examples of PHI PII information include:
- Medical history
- Diagnosis
- Treatment plans
- Prescriptions
- Lab results
- Insurance information
- Patient identifiers (name, SSN, address, etc.)
Why is it so important to keep PII private?
It’s crucial to protect PII information because it safeguards individuals' privacy and helps protect against threats like synthetic identity theft, deep fakes, account takeovers, medical identity theft, extortion, and traditional identity theft. If compromised, it can lead to financial ruin, low credit scores, emotional distress, and legal issues.
How does PII usually get stolen?
PII data can be exposed or stolen through phishing attacks, data breaches, hacking, and unauthorized access to systems storing personal information. A recent FBI study shows that while phishing is the most commonly used tactic for stealing personal information, the reported financial impact of data breaches is much higher.

Here’s a closer look at common ways PII gets exposed:
- Phishing scams: Targets may accidentally reveal personal information by downloading malicious attachments that trigger malware, or clicking on fake links that guide them to spoofed websites. Bad actors often disguise these attacks inside innocuous-looking texts or emails.
- Cyberattacks: Personally identifying information may be stolen via data breaches, ransomware, and man-in-the-middle (MITM) attacks on businesses, individuals, and government agencies. These attacks aim to steal Social Security numbers, account credentials, and other sensitive PII.
- Social engineering: Identity thieves may craft ruses to trick their targets into sharing sensitive information of their own free will. Social engineering tactics can range from simple flattery to complex impersonation schemes.
- Lost or stolen items: Stolen passports or devices, like laptops and smartphones, containing personal data can result in unauthorized access to sensitive information if they’re not properly secured.
7 ways to protect your personally identifying information
If you’re still not sure where to start with protecting your PII, here’s a breakdown:
- Create strong passwords: Use a password generator to create complex passwords or create your own using a mix of upper and lowercase letters, numbers, and symbols.
- Set up two-factor authentication: Use 2FA to help keep your online accounts safe, even if your password gets stolen. Set up biometric safeguards on your phone to help protect your credit cards saved in digital wallets.
- Look out for phishing attempts: Avoid clicking suspicious links or downloading attachments, especially before you have a chance to vet the sender.
- Limit social media sharing: Be cautious about sharing personal information, like your home address, that someone can use to identify you online.
- Secure your devices: Use security software, firewalls, and encryption to protect your devices. And keep your software and apps updated.
- Monitor your finances: Regularly review statements from your bank and credit card for indicators of fraud like unauthorized changes, incorrect balances, and suspicious activity.
- Safely discard sensitive documents: Shred sensitive documents or black out sensitive details with a marker before throwing them away.
- Be careful about using public Wi-Fi: Avoid accessing sensitive information or paying bills on unsecured networks unless you have a VPN to encrypt your connection and help protect the data you send and receive from hackers.
Is your personal information at risk?
While taking proactive measures can limit your risk of falling prey to identity theft, the reality is that no one is completely immune. That's why a robust identity theft protection service like LifeLock Total is essential. By alerting you if your personal information is found on the dark web or has been exposed in known data leaks, LifeLock gives you the time you need to take restorative action, with dedicated U.S.-based Restoration Specialists standing by to assist you along the way.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.





