What is a data breach?
A data breach is an incident where sensitive, protected, or confidential data is accessed or stolen by an unauthorized individual or organization. Data breaches often follow cyberattacks, with hackers breaking into a system to extract information they can sell on the dark web or use to commit fraud.
Data breaches can also be perpetrated by insiders who use their privileged access to release data that’s supposed to be protected. Data breaches are intentional attacks, and they shouldn't be confused with data leaks, which happen when information is accidentally exposed by authorized users.


Data stolen during a data breach can include:
- Online login credentials: Usernames, passwords, and biometric data.
- Personally identifiable information (PII): Full names, dates of birth, addresses, phone numbers, and email addresses.
- Sensitive identity data: Social Security numbers (SSNs), passport numbers, and driving license numbers.
- Financial information: Credit/debit card numbers, bank account details, and billing addresses.
- Healthcare data: Medical records, health insurance details, and information about prescriptions.
If your sensitive data gets exposed in a data breach, you may be at increased risk of fraud or identity theft. Cybercriminals with access could hijack your online accounts, apply for credit in your name, or even steal your medical benefits.
Companies are responsible for protecting the sensitive data targeted in data breaches, and they have a strong incentive to build safeguards against them, given that the average cost of a data breach is $4.9m. Despite this, there were over 3,000 data breaches in 2024 according to the Identity Theft Resource Center (ITRC), putting millions of people’s data at risk.
How does a data breach happen?
Data breaches can stem from diverse attack types, with criminals using strategies like social engineering, phishing, password cracking, and exploiting cybersecurity weaknesses.
A breach typically starts when a hacker identifies an organization that stores valuable user information but has a data security vulnerability. They may try various methods to break in, like sending fake password reset emails to company employees or launching sophisticated cyberattacks.
If they get system access, they aim to escalate their user privileges and find backdoors to sensitive data. When they manage to find a high volume of sensitive information, they begin exfiltrating it to local or cloud storage that they control.
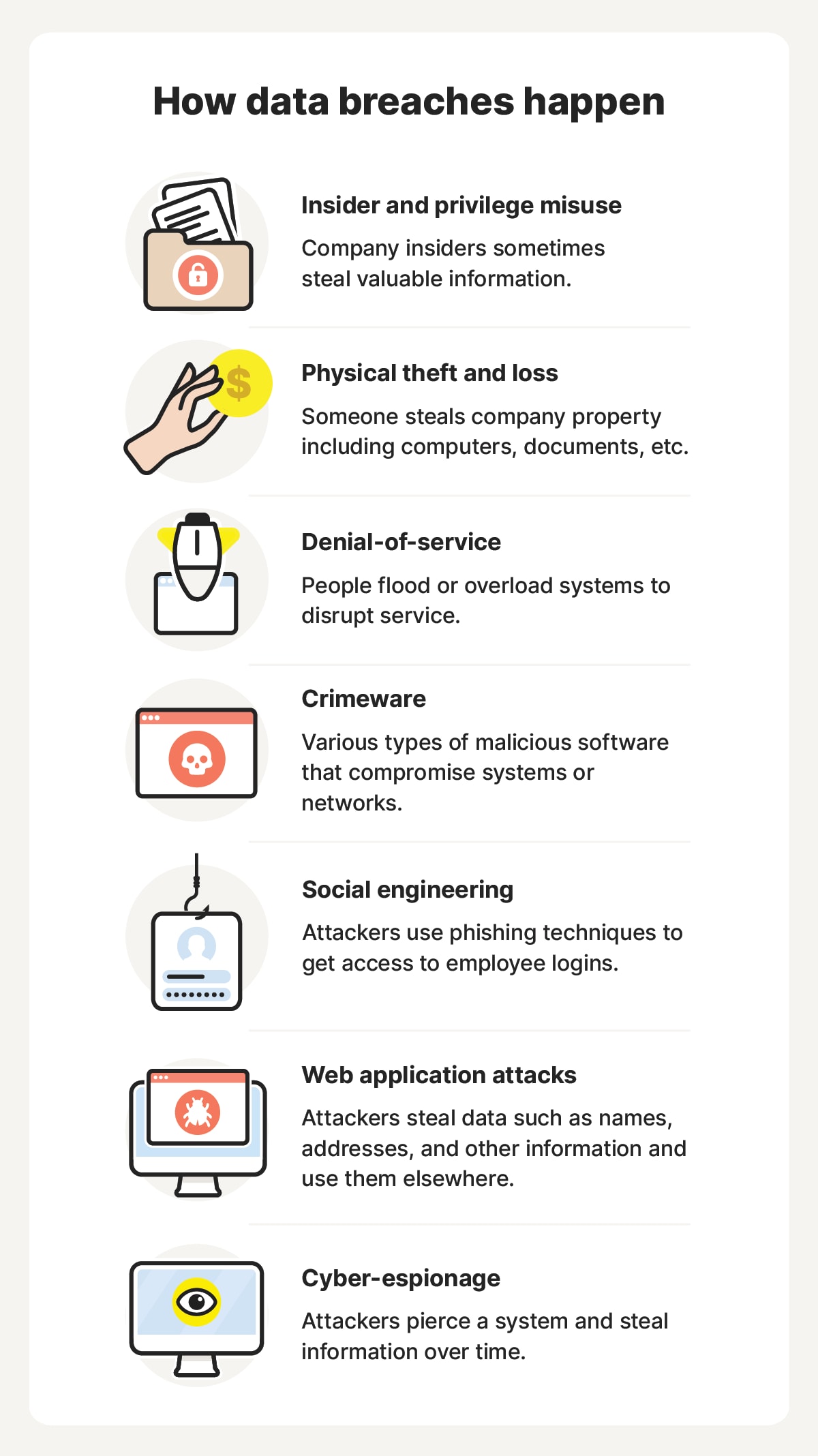

1. Insider and privilege misuse
An insider at an organization can deliberately leak customer or employee information. The motives for internal data breaches aren’t always clear, but perpetrators may commit breaches for financial gain or to inflict harm on the company.
The culprit isn’t always someone with privileged access — it can just as easily be somebody with lower permissions who successfully tricks a coworker or takes advantage of an unattended laptop.
2. Physical theft and loss
An employee misplacing a laptop or phone that contains sensitive data can leave the company exposed to a data breach. If a criminal finds the device, they may be able to access the data and extract it to their own personal computer.
Even lost paperwork can have enough information to constitute a breach. It’s up to companies and individuals to protect any physical items that may represent a data breach risk, taking steps like using secure device passwords and practicing document safety. This is critical for minimizing the likelihood that theft or loss will spiral into something more serious.
3. Denial-of-service
Distributed denial-of-service (DDoS) attacks target organizations by flooding and overloading systems to disrupt services. These attacks are often used as diversionary tactics, designed to distract cybersecurity teams as hackers move on to target sensitive systems.
However, sometimes the DDoS attack is the main threat. They can leave internet services unstable, potentially opening them up to code injection and privilege escalation attacks. Depending on the severity of the DDoS, it may also help mask infiltrations by preventing access logs from being recorded. Crashing a system may also result in a switch to a backup server, which may be less secure and more easily exploitable.
4. Crimeware
Crimeware includes various types of malware that are designed to facilitate sophisticated cyberattacks. Crimeware often spreads through fake emails, malicious files, or links on fake websites. Once installed on a victim’s device, it can operate silently to harvest sensitive information or grant attackers access to larger networks.
Specifically, criminals might use:
- Ransomware: A type of malicious software that identifies and encrypts important files on the target device, with the hacker demanding payment for their release. However, even if payment is made, there’s no guarantee that access will be restored.
- SQL injections: A code injection attack where malicious code is inserted into input fields (like online web forms). As this code passes through the backend database, it can corrupt or manipulate the database, leading to data breaches.
- Keyloggers: Malware designed to record keystrokes made on a device, capable of capturing sensitive information such as usernames and passwords that grant hackers access to systems containing data.
- Botnets: Networks of compromised devices — often infected without the user’s knowledge — that are remotely controlled by cybercriminals and used to launch DDoS attacks.
5. Social engineering
Social engineering attacks exploit human behavior rather than technical vulnerabilities, tricking individuals into revealing sensitive information or granting system access. Phishing is one of the most common social engineering tactics, involving cybercriminals impersonating trusted coworkers, customers, or organizations in deceptive emails, texts, or phone calls.
Phishing attacks are often the entry point for data breaches. If a phisher is able to get access to just one target’s logins, they can move laterally through a network and access valuable data. Alternatively, phishing messages may be used to get an employee to unknowingly install malware on their device, through a malicious link or attachment included in an email, for example.
6. Web application attacks
Web applications, like online banking platforms or e-commerce websites, collect and process large amounts of personal and financial data. Attackers can exploit vulnerabilities in these applications to steal this data at scale, leading to data breaches.
Cross-site scripting (XSS) is one method cybercriminals can use to carry out these attacks. It involves hackers injecting malicious scripts into web pages, potentially allowing them to log keystrokes, steal cookies, or trick users with fake input forms. Attackers may also use SQL injections to get access to web app databases.
7. Cyber-espionage
Cyber-espionage is a hacking strategy that relies on patience, with attackers gaining access to a system and extracting information gradually, instead of all at once, in the hopes of staying undetected. The initial breach often depends on a successful crimeware installation or phishing attack, but once the hacker has access, they’ll stay stealthy.
Unlike other types of data breach, cyber-espionage attacks aim to gain a foothold and then silently escalate privileges. The target data is often high-value, like trade secrets, intellectual property, or national security information, and it’s extracted across months or even years.
Consequences of data breaches
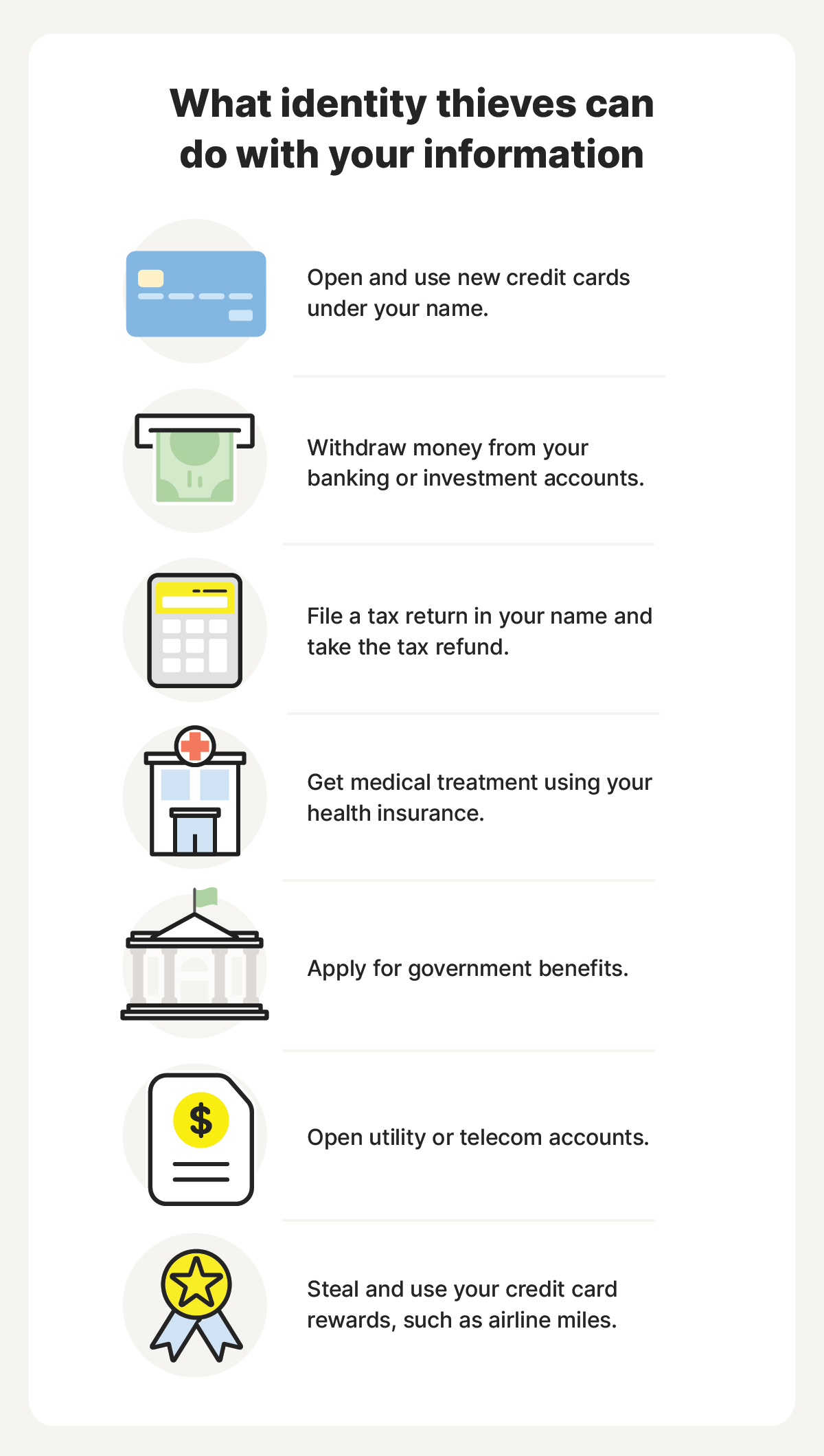
Data breaches have the potential to cause drastic consequences for anyone whose information is compromised. When cybercriminals have access to your sensitive personal or financial information, they can potentially steal your identity, launch account takeover attacks, cause lasting financial harm, and even affect your benefits.
Here’s a summary of some of the follow-up harm you might experience if your data is exposed in a breach and you don’t have the right protection:
- Identity theft: Criminals can use stolen personal information to impersonate you, open fraudulent accounts, or steal your benefits.
- Account takeovers: Hackers with access to your login credentials can hijack your email, banking, or social media accounts, locking you out.
- Credit fraud: Leaked financial data can lead to unauthorized purchases, fake credit card applications, and credit score damage that’s hard to recover from.
- Dark web exposure: Breached data is often sold or given away for free to other cybercriminals or fraudsters on dark web marketplaces.
- Financial losses: Victims of data breaches may experience direct monetary losses if their bank accounts are compromised, and potentially costly recovery processes.
- Emotional distress: Managing the fallout of a data breach, and dealing with the uncertainty it presents, can cause anxiety, frustration, and a feeling of vulnerability.

While you might not have a lot of control over whether your data is being protected in the right way by the companies you share it with, you can take steps to safeguard against the potential consequences of a breach containing your data.
LifeLock can help by alerting you to data breaches that may have impacted your privacy, monitoring for exposure of your personal and financial information on the dark web, and notifying you of potential fraud or identity theft risks, like applications for credit or services made in your name. You’ll also get support from an expert, U.S.-based restoration specialist if your identity is stolen, helping you recover and minimize damages.
Here are four examples of recent, major data leaks that further illustrate the potential consequences of data breaches.
AT&T
An AT&T data breach that took place in 2024 exposed the records of 73 million current and former customers, with exposed information including Social Security numbers, full names, phone numbers, and more. The breached data was later reposted to the dark web, fully decrypted, in June 2025.
This breach exposed millions of victims to the risk of identity theft, and AT&T is set to pay up to $177 million to customers, following class action lawsuits that alleged customer data was inadequately protected.
National Public Data
In April 2024, hackers performed a massive data breach targeting National Public Data (NPD), a data broker whose databases contained billions of personal records, including Social Security numbers and other sensitive information.
The hacking group responsible, USDoD, claimed they had access to 2.9 billion records, which they listed for sale on the dark web for $3.5 million. The breach put millions of people at risk of identity theft and fraud, with NPD ceasing operations in the face of multiple class-action lawsuits.
Texas Department of Transportation
The Texas Department of Transportation suffered a breach of its Crash Records Information System (CRIS) in May 2025, with the data of 300,000 drivers affected.
CRIS contains the personal data of drivers recently involved in car accidents, including their full names, addresses, license plate numbers, insurance numbers, and more. It is believed that the malicious actors used phishing techniques to gain system access.
Marks & Spencer
Hackers breached systems owned by British retailer Marks & Spencer in April 2025, managing to steal names, home addresses, and birthdays. The hackers apparently haven’t shared the leaked information, instead demanding a ransom.
The ransomware brought M&S’s online infrastructure to a halt for months, costing them an estimated £300 million. To break in, hackers used social engineering strategies on a third-party contractor, convincing them that they were an M&S employee who needed a password reset.
Tips to reduce your vulnerability to data breaches
While data breaches typically target large companies, it’s individual users’ data that gets compromised. There’s nothing you can do to reduce the likelihood of a company suffering a data breach, but adopting better data privacy and cybersecurity practices can make you more resilient to the potential consequences of data exposure.
Here are some top tips to reduce your vulnerability to data breaches:
- Minimize the data you share: Be cautious about what personal information you hand over to companies or websites. While it’s tough to avoid sharing anything at all, think critically about whether you really need a service before signing up.
- Use strong passwords: Create strong passwords that contain a mix of uppercase and lowercase letters, numbers, and symbols. Never reuse the same password across multiple accounts to help prevent one data breach compromising your entire online identity.
- Enable multi-factor authentication: Turning multi-factor authentication on for your most sensitive accounts can help prevent cybercriminals with access to your passwords from accessing them, requiring a code sent to your phone or email inbox to log in.
- Monitor your bank statements and credit reports: Fraudsters or identity thieves with access to your personal or financial information may try to take out credit in your name, apply for services with your details, or drain your bank account. Invest in identity theft protection to help detect these threats.
- Reduce your digital footprint: Regularly review your digital footprint by deleting old accounts, scrubbing your social media profiles, and scanning the internet and dark web for your personal data. Reduce your exposure whenever possible to minimize the amount of information cybercriminals may be able to get their hands on.
How to respond to a data breach
Even with all the precautions in the world, you can still be impacted by data breaches. However, acting fast can help minimize the potential risk of fraud and identity theft. Key steps to take after a data breach involving your information include changing passwords for affected accounts, enabling multi-factor authentication, protecting your credit file, and monitoring your online and financial accounts.
Here’s a step-by-step guide to follow in the aftermath of a data breach:
- Confirm the breach: Don’t rely on a text or email alert that could be a phishing attempt. Visit the company’s website or contact customer support to confirm a breach has taken place and ascertain what information was leaked.
- Contact your bank: If your financial information has been compromised, notify your bank or credit card company as quickly as possible to alert them to the risk of fraud and help reduce the risk of financial losses.
- Freeze your credit: If sensitive personal data was exposed, contact the major credit bureaus, Equifax, Experian, and TransUnion, to request a credit freeze or place a fraud alert that will help prevent new accounts from being opened in your name.
- Change your passwords: Update any passwords associated with potentially vulnerable online accounts, choosing new, unique passwords for each account. Also enable multi-factor authentication for an extra layer of security.
- Look out for suspicious activity: Take note of phishing emails, login attempts, or strange transactions in the immediate aftermath of the breach, and continuously review your credit reports for unusual activity or new accounts that you didn’t authorize.
Help protect your data with LifeLock
Companies and organizations aren’t perfect. They may not detect a data breach for months after it happens — and even then, they may be slow to report it. But taking proactive steps to minimize your vulnerability to fraud or identity theft can make a massive difference.
LifeLock includes a range of features that can help you maximize your online privacy, get warnings about data breaches, and detect potentially fraudulent activity — like your Social Security number being used in loan applications. And, if you ever do fall victim to identity theft, U.S.-based restoration specialists are on hand to guide you through the recovery process and mitigate the damage.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.







![How to remove your information from the internet [11 free ways]](/content/dam/lifelock/learn/thumbnails/remove-personal-information-from-the-internet-thumb-2025.jpg)