† Up to $1 million for coverage for Lawyers and Experts, collectively, if needed, for all plans. Reimbursement and expense compensation varies according to plan—up to $1 million for Total, up to $100,000 for Advanced, and up to $25,000 for Core. Benefits under the Master Policy are issued and covered by third-party insurance companies. See GenDigital.com/legal for policy info.
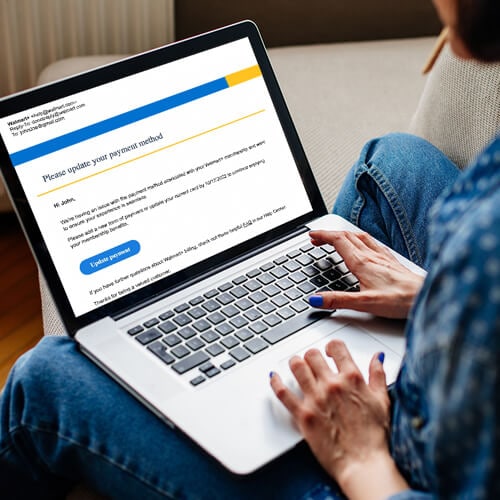
Many people think they’re too smart to fall for phishing emails, until it happens to them. Unfortunately, advances in AI are making some phishing attacks — messages that impersonate trusted brands to steal personal info or money — much harder to detect.
Learn how to tell if an email is a scam, how to protect yourself against threats, and what to do if you accidentally click a link in a fake email.
1. Inconsistent email domains
The first, and often the fastest, way to tell if an email is fake is by checking the sender’s email address. Legitimate companies send messages from their own domain (like @company.com), not public domains like Gmail or Yahoo. Pay close attention to the part after the “@” symbol, where scammers often slip in clever misspellings like “amazom.com” instead of “amazon.com.”
2. Impersonal or unusual language
Most legitimate businesses personalize their emails. In addition to using your name, they also match their tone and style to their usual communication. If something feels off, it probably is. Watch for red flags, such as:
- Unexpected messaging like offers or alerts that don’t match your recent interactions with the company.
- Generic greetings like “Dear Customer” or “Valued User.”
- Inconsistent tone like using overly casual or playful language when they normally speak formally.
But AI is making it easier for scammers to mimic brands in phishing campaigns. Plus, if they’ve obtained your personally identifiable information following a data breach or scraped it from a public source, fraudsters could know a lot about you. That means even emails that seem tailored to you could be fake.
3. Urgent or threatening tone
Scammers love creating artificial urgency to pressure you into acting without thinking. Phishing emails often feature phrases like:
- “Immediate action required.”
- “Pay now to avoid fees and penalties.”
- “Final notice before legal action.”
These high-pressure social engineering tactics are designed to get you to click, download, or share information quickly, against your better judgment.
Trusted businesses typically avoid panic-inducing language and communicate in a calm, professional tone, even when addressing important account matters. For example, a bank might say: “Your payment is overdue. Please log in to your account to make a payment or contact customer service with any questions.”


4. Poor spelling and grammar
Professional organizations invest in quality communications, so authentic emails are usually polished and error-free. Multiple spelling mistakes, awkward phrasing, or obvious grammar errors are strong red flags that you’re dealing with a scammer.
While some types of identity theft schemes now use AI tools to create more realistic emails, other scammers intentionally use poor grammar. They do this to target people who are less tech-savvy and more likely to fall for their schemes. So trust your instincts when something feels off.

5. Requests for personal information
Reputable companies almost never ask for sensitive information through email. If you’re being asked to provide passwords, your Social Security number, credit card details, or other confidential data, that’s a major red flag.
Credible companies already have most of your information on file. They use secure methods to verify your identity when necessary, such as sending a two-step verification code, a push notification through their app, or prompting you to log in to your account through their official website.
6. Inconsistencies or unusual requests
Make sure the email aligns with your recent activities or past interactions with the company. For example, bank scams might involve emails asking for account information that your bank should already have. Unusual payment requests — especially involving gift cards or wire transfers — are also classic scammer tactics.
Legitimate businesses follow predictable patterns in their communications. When something feels out of character for a company you know well, take a moment to verify the request through official channels before responding.
7. Suspicious links or attachments
Unexpected links and attachments are among the most dangerous elements of fake emails. Clicking a malicious link can take you to phishing websites designed to steal your information, while opening an attachment might contain malware that infects your device.
Before clicking anything, always hover over links to see where they actually lead. To do this:
- On desktop: Hover over the link with your mouse to preview the destination URL.
- On mobile: Press and hold the link to view it without opening.
The visible text might say “Contact your bank,” but the real URL could lead somewhere completely different. Be especially cautious of shortened URLs or domains that don’t match the sender’s official website. When in doubt, go to the company’s website directly. Type it into your browser, rather than clicking links in emails because these could be signs of a phishing attack.
8. Unrealistic offers, rewards, or opportunities
If an email promises something that sounds too good to be true, it probably is. Watch for messages claiming you’ve won a competition you never entered, inherited money from distant relatives, or qualified for exclusive investment opportunities with “guaranteed” high returns. Scammers use these enticing offers to grab your attention and override your skepticism.
Similar tactics are used in fake job offers, Publishers Clearing House scams, and various get-rich-quick schemes. Remember, legitimate opportunities usually require effort, time, or investment. They don’t just land in your inbox out of nowhere.
Real-life examples of fake emails
To sharpen your detection skills and learn to spot patterns scammers commonly use, take a look at some real-life examples of fake emails below.
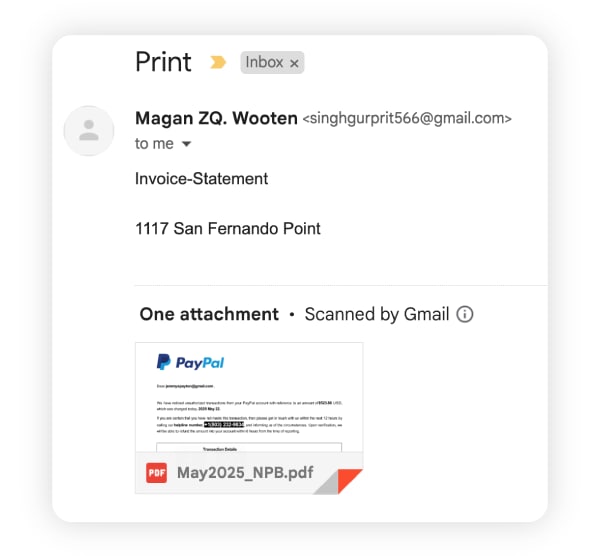
Fake invoice emails
Fake invoice emails claim you owe money for a service you never purchased, often with urgent language like “Payment overdue” or “Final notice.” The sender might use a generic business name and include an attachment labeled “Invoice” that’s actually malware. The goal is to panic you into either paying the fake bill or downloading malicious software.

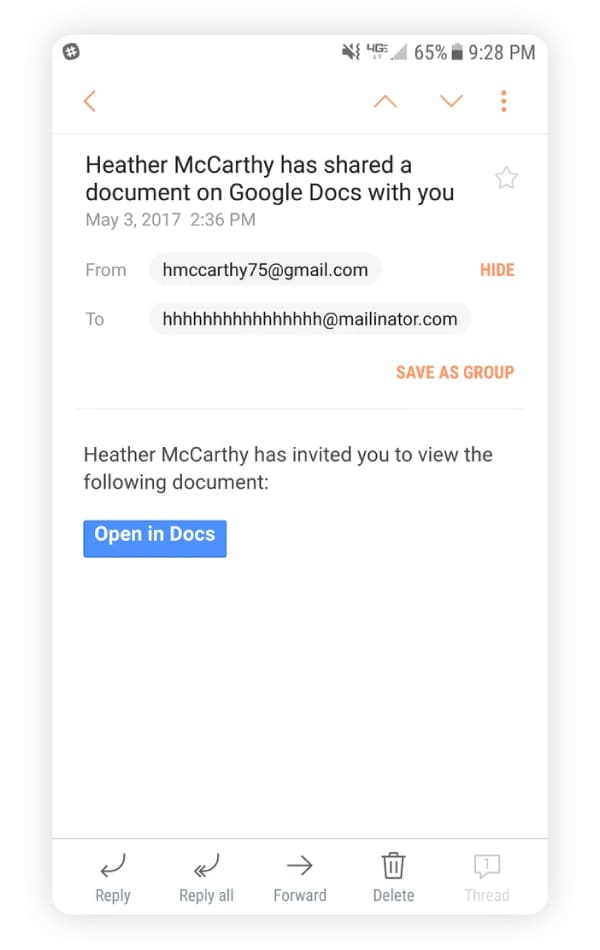
Google Docs scam
This clever phishing attempt looks like a legitimate Google Docs (or Google Forms) sharing notification from someone you know. When you click to view the document, you’re taken to a fake Google login page designed to steal your credentials. Once they have access, the scammer can use your account to send the same fake invitation to all your contacts, spreading the scam further.
In one Reddit post, a user shared how they received a fake email from a beauty brand looking for people to review their products. The email contained a Google Forms link, which they filled out, capturing their personal details, like their name, address, and Google login.

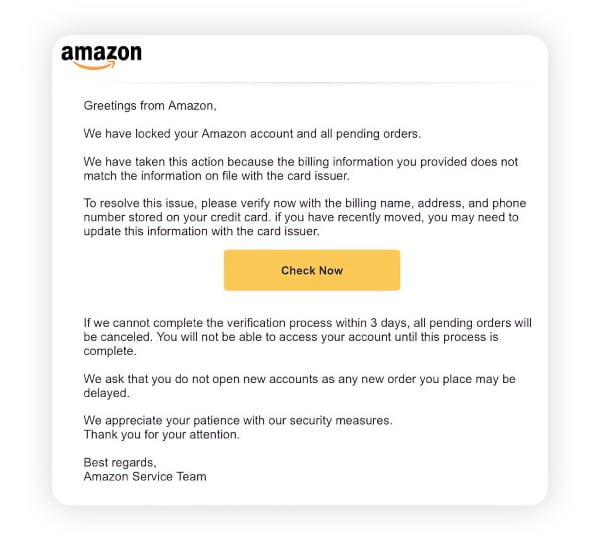
Fake email from Amazon
These phishing messages are Amazon scams, often claiming there’s a problem with your recent order or account, complete with official-looking logos, formatting, and even fake tracking numbers. While they may appear legit at a glance, they usually come from an email address that doesn’t match Amazon’s official domain, and the links inside often lead to phishing sites that steal your login credentials or payment details.
A Reddit user shared a story about nearly falling for a spoofed Amazon email that prompted them to call a fake support number. The email was convincing enough that they even tried to log into their account and provided their credit card’s CVV code. While they ultimately locked their card and didn’t see suspicious activity, the experience highlights how believable these scams can be.
If you’re using Gmail, there’s a simple way to check whether an email is genuinely from Amazon. Tap the small arrow next to the sender’s name and choose “View security details.” If both the “mailed by” and “signed by” fields show amazon.com, it’s most likely authentic. If they don’t, the email is likely spoofed and should be deleted and reported.

How to protect yourself from fake emails
Taking proactive steps can significantly reduce your exposure to email scams and help protect against identity theft. Here are several ways to stay safer and help avoid phishing attacks:
- Add spam filters to your email: Most email providers offer built-in spam filtering that automatically moves suspicious messages to a separate folder. Enable these filters and adjust their sensitivity settings to catch even more potential spam before it reaches your inbox.
- Don’t respond: Never reply to suspicious emails, even to tell the sender to stop contacting you. Responding confirms that your email address is active, which can lead to more spam and targeted attacks.
- Verify the sender: When you receive unexpected emails from companies or contacts, verify their authenticity by contacting them directly through official channels. Use phone numbers or websites you trust, not contact information provided in the suspicious email.
- Don’t click any links or open attachments: Navigate to websites directly by typing URLs into your browser rather than clicking email links. Avoid opening unexpected attachments, especially executable files (usually end in .exe or .app) or documents from unknown senders.
- Install cybersecurity software: Comprehensive security software can help detect and block malicious emails, links, and attachments before they cause problems. Keep your software updated to protect against the latest threats.
- Use dark web monitoring services: If your personal info, such as your email is on the dark web, you may see an increase in targeted spam and phishing attempts. LifeLock’s powerful dark web monitoring feature can help you identify if your information has been leaked. And if your data is exposed, LifeLock will help you take important steps, like changing your passwords, to keep your accounts safer.
In addition, if your identity is ever compromised, LifeLock’s Million Dollar Protection Package can provide up to $1 million† in coverage for lawyers and experts.
What to do if you responded to a fake email
Don’t panic if you’ve already interacted with a suspicious email, but quick action can help minimize any potential damage.
- Don’t reply again: Resist the urge to send follow-up messages, even if you want to express anger or demand removal from their list. Additional responses only confirm your email is active and monitored.
- Change any passwords you revealed: If you entered login credentials on a fake website, immediately change those passwords on the legitimate site. Use strong, unique passwords for each of your accounts to improve password security and help prevent further unauthorized access.
- Contact your bank or financial institution: Alert your financial institutions immediately if you provided credit card numbers, bank account details, or other sensitive information. They can help you monitor for fraudulent activity and may need to issue new cards or account numbers.
- Scan for malware: Run a complete system scan with updated antivirus software to check if any malicious programs have been installed. Remove any detected threats and consider professional help if your computer is behaving strangely.
- Report the email: Forward suspicious emails to your email provider’s abuse department and consider reporting them to the FTC or other relevant authorities. This helps improve filtering systems and can assist in tracking down scammers.
- Monitor your accounts: Keep a close eye on your bank statements, credit reports, and other financial accounts for unusual activity.
- Freeze your credit: If you shared sensitive information, like your Social Security number, or other data that criminals can use to open new accounts, consider placing a credit freeze and fraud alert with the three major credit bureaus. This helps prevent scammers from opening new lines of credit in your name.
- Sign up for identity theft protection: Identity theft protection can help monitor your personal information across multiple channels and alert you to potential misuse. Services like LifeLock offer monitoring and alerts that can help protect against identity theft and support you if your info is compromised.
Protect yourself against fake emails
Fake emails can be convincing, so knowing how to spot the warning signs can make a big difference.
But protection doesn’t stop there. For added peace of mind, use a service like LifeLock. LifeLock monitors the dark web for your personal information, alerts you to suspicious activity on your accounts that could affect your credit, and helps you respond quickly to potential threats. And, if your identity is stolen, LifeLock offers expert support through U.S.-based restoration specialists who can help you recover.
FAQ
How do I stop fake emails?
You can’t completely stop scammers from sending fake emails, especially if your email address has been leaked in a data breach, but you can help reduce phishing attacks in the future by enabling your email provider’s spam filters.
How do you check if an email is real?
To check if an email is real, verify that the sender’s email address matches the company’s official domain, hover over links to check their destinations, and contact the company directly through official channels if you’re unsure. Look for personalization, professional formatting, and reasonable requests that align with your relationship with the sender.
What happens if you open a fake email?
If you open a fake email but don’t interact with it, there’s usually no harm done. However, interacting with a fake email — by clicking links, downloading files, or entering personal information — can lead to malware infections, compromised accounts, or even identity theft.
How do you check a suspicious email without opening it?
To check a suspicious email without opening it, look at the sender’s address, subject line, and any preview text visible in your inbox. Check if the sender and subject align with the type of email you’d expect to receive.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- 1. Inconsistent email domains
- 2. Impersonal or unusual language
- 3. Urgent or threatening tone
- 4. Poor spelling and grammar
- 5. Requests for personal information
- 6. Inconsistencies or unusual requests
- 7. Suspicious links or attachments
- 8. Unrealistic offers, rewards, or opportunities
- Real-life examples of fake emails
- How to protect yourself from fake emails
- What to do if you responded to a fake email
- Protect yourself against fake emails
- FAQ
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.