December 2025 update: 700Credit, a company that handles credit checks for car dealerships across the U.S., has confirmed a data breach. Hackers stole the personal information of more than 5.6 million people, including names and Social Security numbers. If exploited, criminals can use this information to commit identity theft.
How LifeLock can help: With LifeLock identity theft protection, you get an alert if we find your information on the dark web or detect signs of identity theft on your credit report. And if you become a victim of identity theft, LifeLock will fix it — guaranteed.*
Data breaches can affect both large companies — like the 2024 National Public Data breach that exposed an estimated 2.9 billion records and the AT&T breach that impacted more than 70 million customers — and small local businesses. Regardless of the company’s size, when sensitive user data is exposed to potentially malicious parties, individual victims are left dealing with the consequences.
The sudden realization that a cybercriminal has access to private details about your life is unsettling, to say the least. But the good news is that it’s not the end of the world — you still have options to protect yourself against data breach identity theft, and there are ways to recover your identity if you were already attacked.
Whether it’s your Social Security number (SSN), bank account logins, employment information, location coordinates, medical or school records, or other personal data that’s exposed, you need to take proactive steps to help protect your identity. In this article, we’ll help you learn how to recover from a data breach with nine easy-to-follow tips.
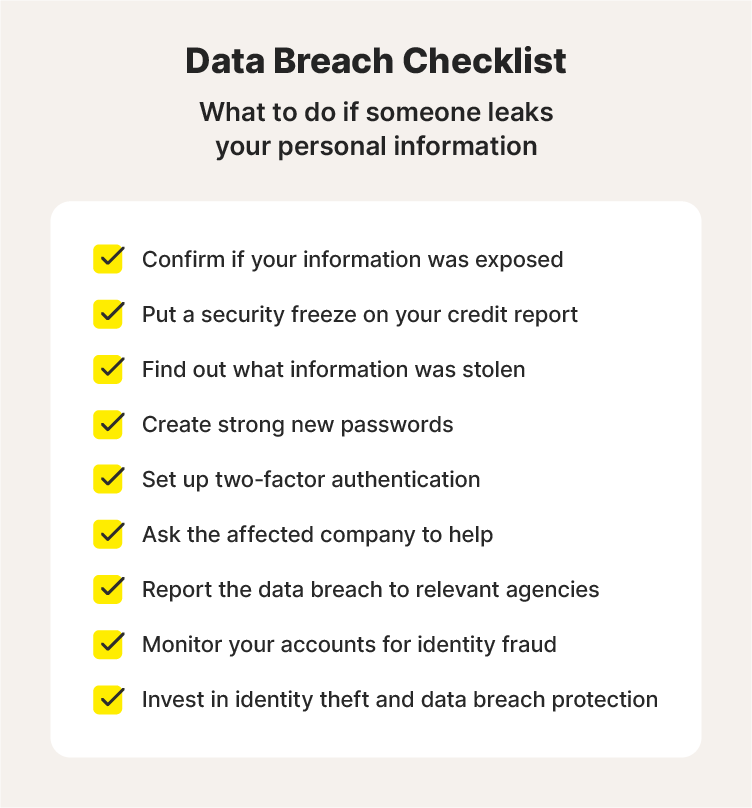

1. Confirm if your information was exposed in a data breach
The first step is to confirm that a breach involving your data actually occurred. Although the impacted organization may notify affected users after suffering a breach, you might not hear about it immediately. Even if you do, a data breach notification isn’t always legitimate. For all you know, it could be a phishing scam someone is using to convince you to voluntarily give up sensitive information.
However, if you read in the news about a company you’ve shared data with experiencing a data breach, get a notification from your data breach monitoring tool, or notice suspicious anomalies in your finances or personal accounts, contact the organization immediately using an official channel to learn more.
What to do: Safely determine whether or not your data was compromised in a data breach by visiting the affected organization’s website to look for an update or by contacting their customer service directly.
2. Freeze your credit
Credit freezes restrict access to your credit report, helping prevent unauthorized people opening new lines of credit in your name. Freezing your credit after a data breach that exposes your Social Security number, financial information, or personal details makes it more difficult for anyone with access to the information to use it to fraudulently open accounts or make purchases.
That’s because lenders, property managers, real estate agents, and anyone selling big-ticket items need to see your credit history before they can approve a contract or purchase. With a freeze in place, creditors will be unable to perform this check. You can then consider unfreezing your credit once the threat posed by the breach has diminished.
What to do: Contact the three major credit bureaus — Equifax®, Experian®, and TransUnion® — online or by phone, and officially request a credit freeze.
3. Determine what information was stolen
While having any personal data exposed is bad news, not all data breaches are equally threatening. Some types of data are more sensitive than others, putting you at direct risk of fraud and necessitating a more robust protection and recovery effort.
For example, stolen credit cards can easily be canceled and replaced, and stolen funds can quickly be disputed. But getting a new Social Security number can be extremely difficult if yours is compromised. Not only that, but a fraudster with access to your SSN could cause lasting problems by committing crimes or opening new accounts in your name.
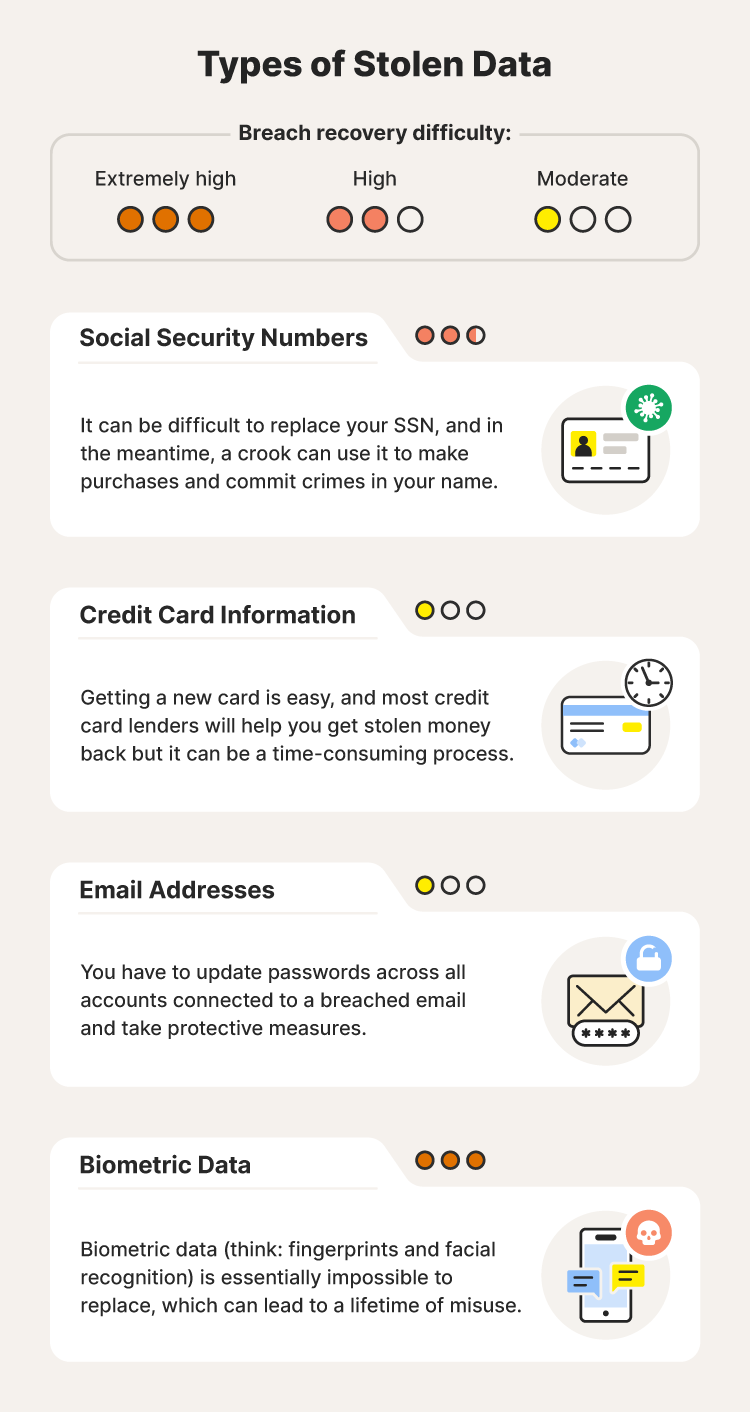

What to do: Contact the company that experienced the data breach and review their breach disclosure statements. You should be able to find out what information was stolen, whether it’s financial details, personal identifiers, login credentials, or something else.
4. Change your passwords
After a breach, it's important to change your online login information, including your passwords and security question answers, as soon as possible. This will help prevent anyone with access to your login information getting into your accounts and stealing more data.
Don’t limit this to only the affected account. Take the time to update your login credentials for all your sensitive accounts, and use long and unique passwords to help boost your password security. This will help prevent cybercriminals from accessing your other accounts and getting more information about your finances and personal life.
What to do: Change your login information for the affected account and any other potentially compromised accounts, choosing new, strong, and unique passwords. If you have the option, force every connected device to log out of your accounts when you update your passwords to kick unauthorized users off.
5. Enable two-factor authentication
Two-factor authentication (2FA) is a security measure that adds an extra layer of identity verification to the login process, building on the security a strong password offers. After entering a password, the 2FA login process will typically either require a code (sent to a secure device via text or email) or biometric data (such as a fingerprint or face scan).
Enabling 2FA on the compromised account and other potentially vulnerable accounts can help protect your personal information and identity from future attacks or fraud attempts by making it harder for cybercriminals to get into your account — even if they have your password.
What to do: Log into the affected account, navigate to the security and privacy settings, and look for the option to set up two-factor or multi-factor authentication. If it’s an option, the site will guide you through linking your account to the secondary authentication method.
6. Get help from the company affected by the data breach
If the breached company offers to help repair the damage and protect you for a certain amount of time, consider taking them up on it.
In most cases, a lack of security safeguards or personnel training cause security breaches in companies — and they will help resolve the issue. Beyond that, they likely have procedures to help customers recover their accounts, money, and anything else that is stolen in an attack.
What to do: Seek support from the company that lost your information by using their dedicated response teams to learn more about new security measures and receive help to recover from the breach or identity theft faster.
7. Report the attack
You should report the data breach and resulting identity theft to the appropriate parties. If you aren’t sure whether the breached company is aware of the problem, contact them if you haven’t already. Doing this right away can help limit the damaging effects of the leak.
Other than the impacted business, you should also notify your bank and credit card companies as a preventative measure. If the breach resulted in you losing sensitive personal information, like your Social Security number, or financial details, like your credit card number, you could be more vulnerable to identity theft or fraud.
What to do: If you’re a victim of identity theft, consider freezing your credit with the credit bureaus and file an identity theft report with the FTC online at IdentityTheft.gov or by phone at (877) 438-4338.
8. Monitor your accounts closely
Monitoring your online accounts and credit reports after a data breach can help you spot suspicious activity to catch the early stages of fraud or identity theft. The warning signs of an account takeover attack or identity theft may include settings or password changes, unexpected purchases, or unauthorized account updates.
You can also obtain your free credit reports from AnnualCreditReport.com to look for activity you don’t recognize.
What to do: Monitor your online accounts and credit reports to detect identity theft attempts early. You can use a credit monitoring service like LifeLock that helps you track key changes to your credit file at a leading credit bureau and alerts you if strange account behavior is detected.
9. Invest in identity theft and data breach protection
Identity theft and data breach protection software offers a combination of features that add an extra layer of defense against the risks of fraud or identity theft following a data breach. It can help you proactively monitor your credit, protect your identity, and keep your financial health in shape — valuable features that can provide support after a data breach or help you protect against the consequences of future breaches.
What to do: Consider a service like LifeLock that can help you protect your personal information, notify you when cybercriminals sell your data on the dark web, and monitor your credit activity with a major bureau.
Secure your online identity
Today, cybercriminals seem to constantly invent new ways to steal and profit from personal data. That’s why it’s more important than ever to practice good digital hygiene and put protections in place for incidents like data breaches that are out of your control. Become a LifeLock member to help protect against identity theft and get the support you need if you do become a victim.
FAQs
How do I know if my personal information was compromised?
It depends. Most people discover that somebody stole their information after unusual account activity, unexpected transactions, or a breach notification. If a company is aware that somebody stole your data through their website, product, or application, they will generally publish a statement and send out a notification to users.
Some other warning signs of a data breach and identity theft include:
- New account sign-ups
- Old accounts being closed unexpectedly
- Account lockouts
- Suspicious transactions on your bank statements
- Sudden drops in your credit score
- An uptick in subscriptions and junk mail
- Unexpected notifications
- Unsolicited password reset notifications
What companies have experienced data breaches?
Unfortunately, data breaches are more common than you might think. Here are a few examples of data breaches involving well-known companies or organizations:
- National Public Data (2024)
- AT&T (2024)
- Microsoft (2019)
- Chipotle (2017)
- Equifax (2017)
- Uber (2016)
- Target (2013)
How can your friends be affected if your information is stolen?
Cybercriminals can use stolen personal data to defraud your friends and network through phishing and other social engineering attempts. Those tactics can be more successful than general scams because people who know you are more likely to trust you and willingly share private information or click a link.
*Restrictions apply. Automatically renewing subscription required. If you are a victim of identity theft and not satisfied with our resolution, you may receive a refund for the current term of your subscription. See Lifelock.Norton.com/Guarantee for complete details.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- 1. Confirm if your information was exposed in a data breach
- 2. Freeze your credit
- 3. Determine what information was stolen
- 4. Change your passwords
- 5. Enable two-factor authentication
- 6. Get help from the company affected by the data breach
- 7. Report the attack
- 8. Monitor your accounts closely
- 9. Invest in identity theft and data breach protection
- Secure your online identity
- FAQs
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.