Some estimates suggest the dark web makes up just 0.01% of the internet, yet it’s the epicenter of online identity theft–related fraud. Dark web marketplaces host many identity-related listings that can enable identity theft, from “fullz” (or full identity profiles) to individual Social Security numbers, passports, or credit card details. On top of that, billions of stolen account credentials have been leaked and traded in these marketplaces.
Read on to learn what types of information dark web scans can find, how they find it, and which dark web scanners you should use.
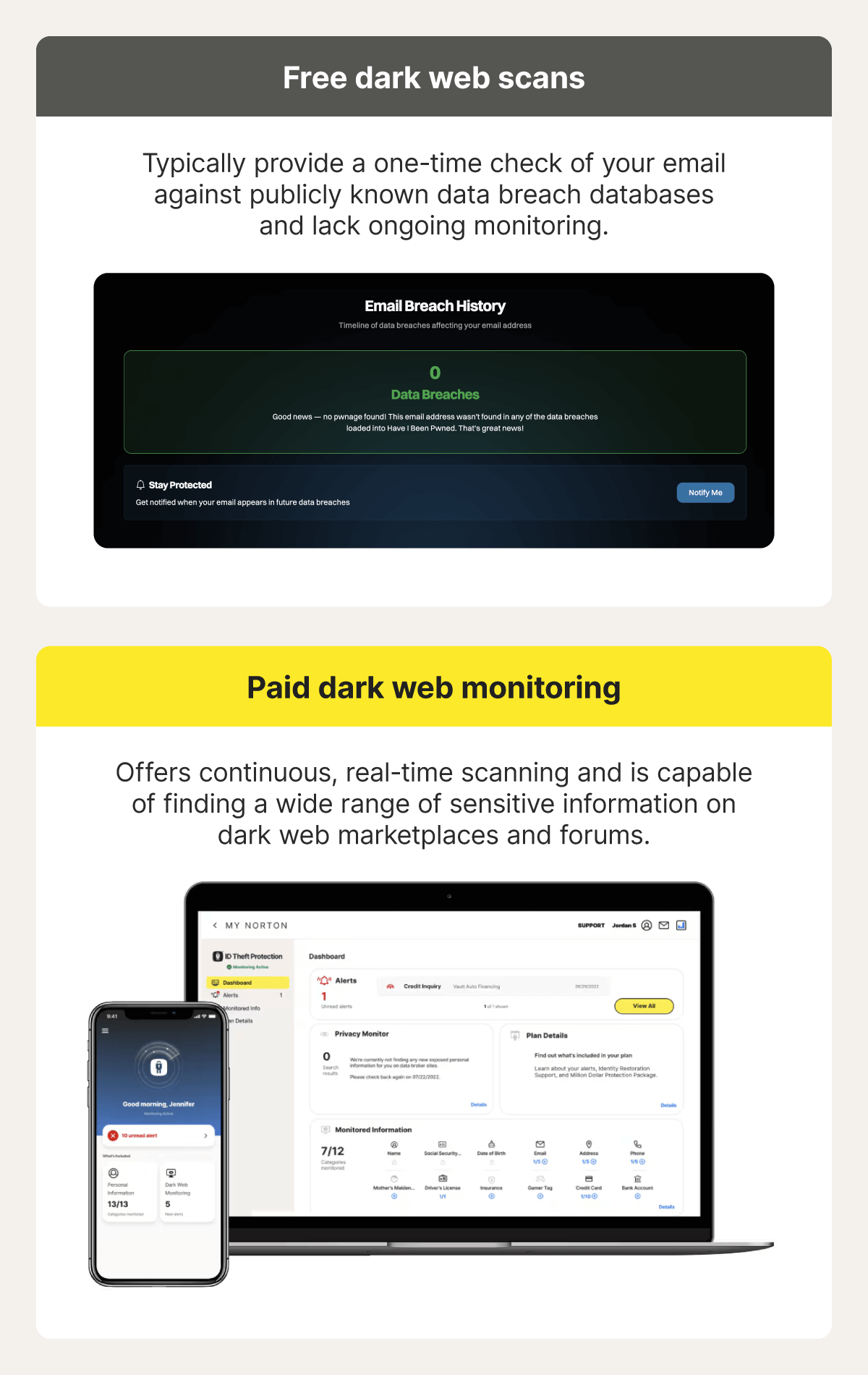
What is a dark web scan?
A dark web scan is a security feature that searches known dark web forums, marketplaces, and breach databases to see whether your personal information has been exposed or traded. It typically looks for data like email addresses, passwords, Social Security numbers, and credit card details that may have been leaked through data breaches or malware infections.
While you can’t remove information from the dark web once it’s been shared, a dark web scan can help you spot exposure early, so you can take timely steps to reduce the risk of identity theft or fraud, such as changing passwords or freezing your credit.
Dark web scanning vs. dark web monitoring
A dark web scan is typically a one-time or occasional check that you trigger manually, and it lets you know if your information is already exposed. Dark web monitoring is a similar feature that runs continuous scans to alert you as soon as your information is detected on the dark web, potentially after being exposed in a data breach.
Here’s a side-by-side comparison to help you understand the difference:
Dark web scan |
Dark web monitoring |
|
|---|---|---|
Frequency |
A single, on-demand lookup. |
24/7 ongoing monitoring. |
How it works |
Scans the dark web, forums, and breach databases at the time you prompt the check. |
Continuously scans the dark web, forums, and breach databases. |
Good for |
Quick checks to see if your information is currently exposed. |
Early notification and proactive protection. |
How do dark web scans work?
Dark web scanners use a mix of automated web crawlers, pattern matching, and AI-assisted analysis to search known dark web sites, such as breach dumps, paste sites, forums, and marketplaces, for exposed personally identifiable information (PII), account credentials, and other sensitive details linked to you.
However, dark web sites frequently change addresses, shut down, or block bots with CAPTCHAs. Many forums are private or invitation-only, and some data is shared briefly before disappearing. As a result, dark web scans can reduce risk and improve visibility, but they can’t guarantee complete coverage.
How to choose a dark web scanning service
A worthy dark web scanning service should monitor multiple types of personal data, deliver timely alerts with clear guidance, fit your budget, and offer reliable customer support. Ideally, your chosen service will also include identity theft protection and recovery features.
So, before you subscribe, confirm that your chosen dark web scanner:
- Monitors for a wide range of data: It should search for your name, Social Security number, driver’s license number, physical and email addresses, phone numbers, bank account numbers, credit card numbers, and more.
- Provides guidance: If a scanner detects exposed data, it should clearly explain what it found and share actionable next steps to help you secure your accounts and data.
- Is secure: Because you have to provide sensitive data so the scanner knows what to search for, you should confirm it has strong encryption and safe data handling practices.
- Strikes a balance between price and value: Free dark web scanning tools can offer limited insight, but they’re often less reliable and comprehensive. Paid services typically use more advanced technology, allowing them to scan a wider range of sources and identify newer exposures.
- Bundles features: Look for add-ons like credit monitoring, stolen funds and expense reimbursement coverage, and restoration assistance that can help you if your exposed data is used by cybercriminals to commit identity theft.
- Provides customer support: Choose a service with accessible, 24/7 support, ideally offering options like phone and chat that provide fast, clear assistance.

Dark web scanners you should use to stay on top of threats
There are several reputable dark web scanning tools around, each with its own strengths. Here are some of the best free and paid options, starting with the most comprehensive.
LifeLock dark web scanner: Best for continuous monitoring and alerts
LifeLock is much more than a dark web scanner, offering comprehensive dark web monitoring, which continuously scans hidden sites and forums for more than 120 types of personal information and identity elements, including:
- Your name
- Mother’s maiden name
- Social Security number
- Birth date
- Driver’s license number
- Physical addresses
- Email addresses
- Phone numbers
- Bank account numbers
- Credit card numbers
- Insurance
- Gamer tags
This makes it a strong option for proactive users who want to be made aware of data exposure as soon as it’s detected so they can take preventive steps before somebody misuses their information.
Some other benefits you get with LifeLock include data breach notifications, digital footprint monitoring, identity theft restoration support, and a reimbursement package which can help cover losses and expenses resulting from identity theft.
Have I Been Pwned: Best for identifying email address exposure
Have I Been Pwned (HIBP) is one of the most trusted free data breach checkers available. While it doesn't directly scan the dark web, it cross-references your information against a vast database, flagging accounts compromised in known breaches.
HIBP is best used to quickly and easily detect the exposure of specific sensitive data, such as email addresses and passwords, that cybercriminals are likely to trade on the dark web.
Google dark web report: Best for free and basic checks
Built into Google accounts, the Google dark web report provided a quick assessment of data on the dark web associated with your email address or other information you shared with your monitoring profile, such as:
- Your name
- Address
- Phone number
- Username
- Password
It was free, fast, and useful for basic exposure checks, but doesn’t offer in-depth, ongoing monitoring. However, the decision was made to discontinue the free tool early in 2026, and it’s unavailable as of February 16th 2026.
How to run a dark web scan
Running a dark web scan is a similar process across most tools. You create an account and enter the details you want to check, such as your email address, Social Security number, or credit card information. Depending on the service, the tool will either deliver a one-time assessment or continuously monitor for signs that your information has been exposed.
LifeLock’s dark web monitoring feature is a comprehensive and reliable option that can do both. As well as repeatedly scouring the dark web for subscribers’ compromised data, you can also run a free one-time, deep-dive personal data exposure scan right now by following these simple steps:
- Enter your email: Type your email address into our free personal data exposure scanner and click “Run your free scan.”
- Share identifying details: Input your full name, city, and state to enable a more complete exposure scan.
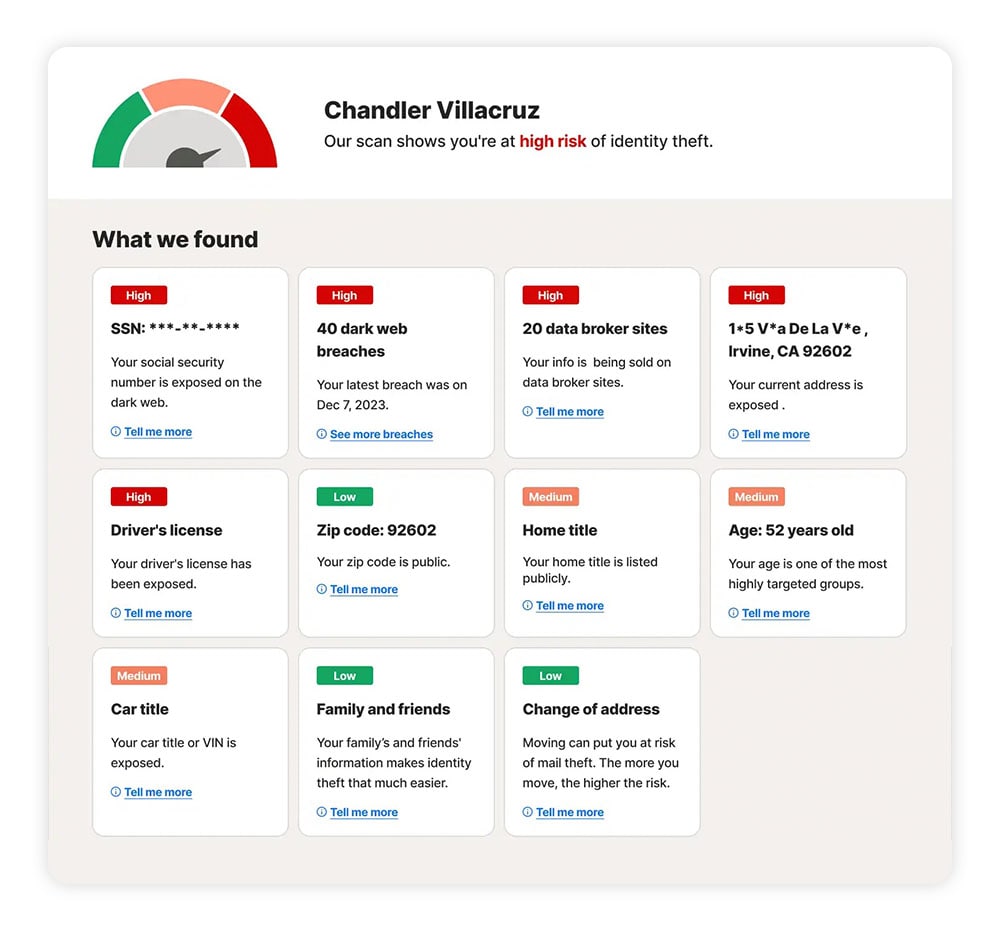

From there, you’ll receive a personalized risk assessment and a detailed breakdown of the scanner’s findings. This report will clearly show if sensitive identifiers, such as your SSN, address, driver’s license number, home or car title, or ZIP code, have been exposed.
The report also clarifies whether your information is on the dark web or on data broker websites used for targeted marketing, background checks, and identity profiling.
What to do if your personal information is on the dark web
If a scan shows your information circulating on the dark web, act quickly to reduce the risk of identity theft and fraud. A quality dark web monitoring service will usually provide tailored recommendations, but these immediate steps can help strengthen your protection right away:
- Change passwords: Update passwords for exposed accounts and other accounts that use similar credentials, starting with your email and financial accounts. Create strong, unique passwords for each account, and consider using a reputable password manager to store them securely and reduce the risk of future breaches.
- Enable identity authentication: Turn on two-factor authentication (2FA) or multi-factor authentication (MFA) for all sensitive accounts, including email, banking, and social media. This adds a critical layer of protection even if attackers already have your password.
- Alert financial institutions: Contact your bank, credit card issuer, or brokerage to report the exposure. Ask them to close compromised accounts, issue new account numbers, and monitor for suspicious activity.
- Report to authorities: If you find evidence of identity theft (like unauthorized account openings), file a report at IdentityTheft.gov to create an official recovery plan, and file a report with your local police.
- Monitor financial and medical statements: Review bank, credit card, insurance, and medical statements regularly for unfamiliar charges or services. Criminals often start with small, less noticeable transactions to test whether an account is active.
- Check your credit report: Request free credit reports from all three bureaus — Experian, Equifax, and TransUnion — through AnnualCreditReport.com. Look for unfamiliar accounts, inquiries, or debts.
- Freeze your credit: Place a credit freeze with each of the three major credit bureaus to prevent criminals from opening new credit accounts in your name.
Scan the dark web for identifying information
Looking for comprehensive dark web scanning for ultimate peace of mind? Subscribe to LifeLock for ongoing dark web monitoring that scours hundreds of millions of data points a second. As well as getting notified when your data is found on the dark web, you’ll benefit from a wide array of identity protection tools and access to expert support if your identity is ever compromised.
FAQs
How reliable are dark web scans?
Dark web scan results are generally reliable, but they’re rarely complete. The dark web is vast, decentralized, and heavily encrypted, which means no tool can scan 100% of its content.
Do I need to provide personal information to initiate a dark web scan?
Yes, dark web scanners need specific personal details to know what to search for. This may include your email address, Social Security number, credit card information, full name, or phone number.
How often should I run dark web scans?
Subscribing to continuous dark web monitoring is the most effective option, as it notifies you quickly once your sensitive information is discovered, helping you take action to head off identity threats. If you rely on a free tool instead, aim to run a scan ideally once a week, at least once a month.
Can I take my information off the dark web?
In most cases, no. Once data is leaked on the dark web, it generally can’t be removed. The best defense is to limit the damage by securing your accounts, freezing your credit, and monitoring for misuse.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.





![How to remove your information from the internet [11 free ways]](/content/dam/lifelock/learn/thumbnails/remove-personal-information-from-the-internet-thumb-2025.jpg)

