What the experts say
"The center of gravity in cybercrime is people... Criminals are working to walk users into traps that look and feel legitimate." - Gen 2025 Threat Report
Threat Research Team, Gen
Social engineering is one of the most prevalent cybercriminal tactics. According to a recent Gen Threat Report, many online attacks either begin with social engineering techniques or leverage them to spread malware.
Social engineering is a tactic cybercriminals use to manipulate people into divulging personal information or performing actions that compromise security. Instead of directly targeting technical systems, social engineering attacks exploit human behavior, playing on emotions like fear, trust, curiosity, or pity to steal personal and financial information.
What the experts say
"The center of gravity in cybercrime is people... Criminals are working to walk users into traps that look and feel legitimate." - Gen 2025 Threat Report
Threat Research Team, Gen
Once they obtain the information they’re after, social engineers can access sensitive accounts, engage in corporate espionage, commit fraud, blackmail their victims, or sell the data on the dark web.
Social engineers usually communicate directly with their victims to manipulate them into compromising their security. They may also create fake websites and pop-ups to convince large numbers of victims to hand over money or information.
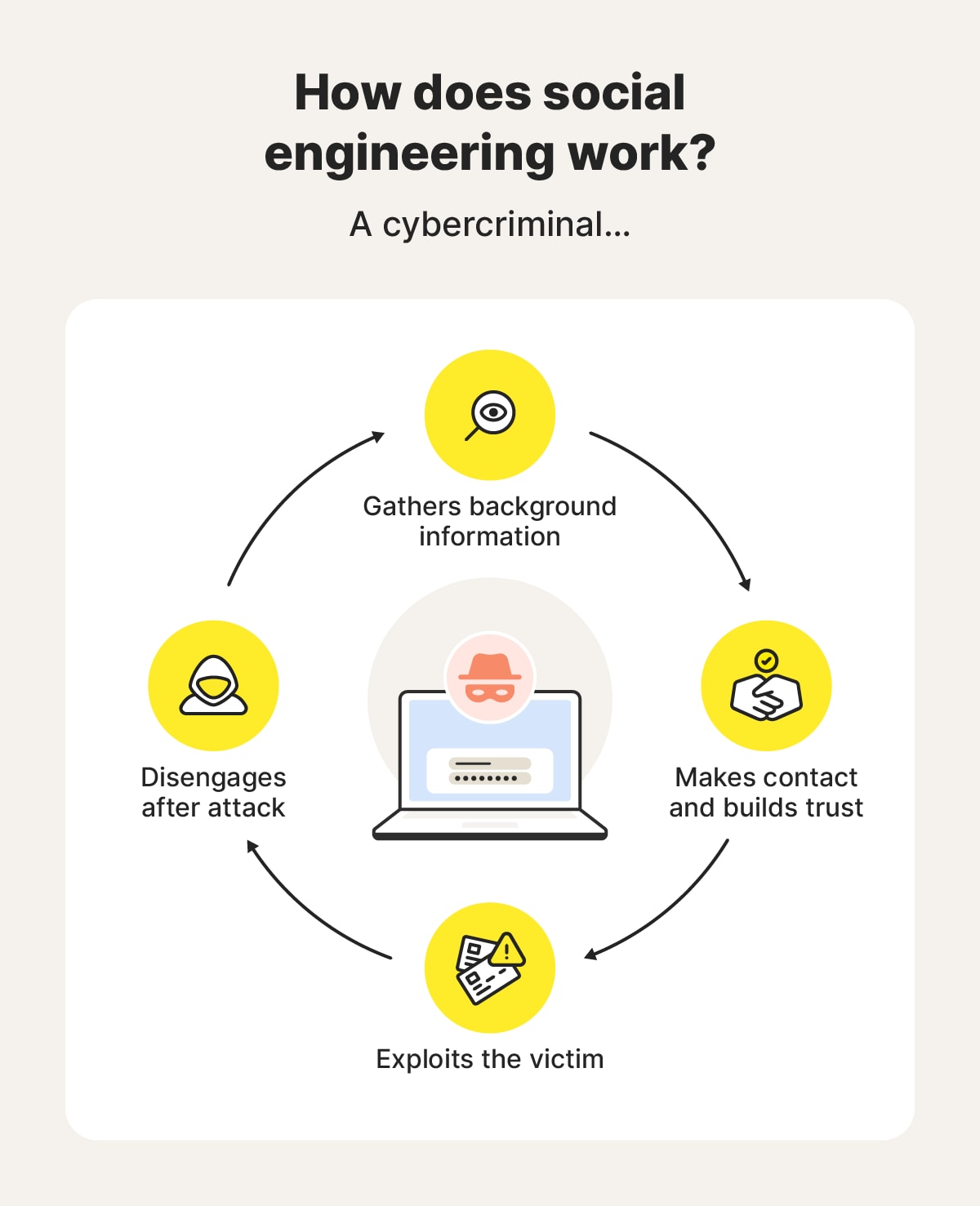
Social engineering typically involves the following steps:
Cybercriminals begin by gathering personal information about their victims. They may purchase data on the dark web, scour publicly available sources like social media profiles or data brokers, or exploit data breaches.
They might also use phishing emails, fake surveys, or spoofed websites to trick individuals into revealing personal details to launch a more targeted social engineering attack.
Once the social engineer has enough information, they initiate contact via email, text, phone, or social media. They will typically pose as trustworthy figures or entities and use the information collected in step one to build credibility.
Next, the cybercriminal exploits the victim’s emotions and manipulates them into clicking a malicious link, sending money, or revealing sensitive information. They may offer an exclusive reward, claim they need urgent help, threaten to close their victim’s accounts, or warn of large charges or fees. The goal is to pressure the victim into acting quickly without fully considering the consequences.
When the cybercriminal has stolen money, infected a device with malware, or obtained whatever information they were after, they disengage, often leaving the victim unaware of the breach until it’s too late.

Attackers use multiple social engineering tactics to trick individuals into compromising their security. Here are examples of nine common social engineering schemes.
In phishing attacks, cybercriminals use fake emails, websites, calls, or messages to trick individuals into sharing sensitive information like login credentials or financial details. These scams often imitate trusted brands, like Geek Squad, creating a sense of urgency with messages like “Your account is at risk” or “Immediate action required.”
Numerous scams fall under the phishing category. Here are a few common types of phishing attacks.
Cybersecurity tip: One way to identify phishing emails or text messages is poor spelling and grammar. Legitimate organizations work with professional copywriters to ensure communication is clear and error-free.
Baiting is a social engineering tactic where scammers lure people into downloading malware or sharing personal information by piquing their curiosity or using tempting offers like exclusive deals or free downloads. Once downloaded, the malware can steal personal data that scammers can sell on the dark web or use to commit various types of identity theft.
Criminals use multiple baiting techniques to trick individuals. Here are a few common types of baiting attacks:
Cybersecurity tip: If something sounds too good to be true, it probably is. Be cautious of deals or offers that seem overly generous, especially from unfamiliar sources.
Diversion theft is a type of social engineering scheme where criminals trick couriers or delivery services into sending packages to the wrong person or place. They do this by impersonating someone from the delivery company, or the recipient, and convincing the target to change or confirm the wrong details.
Cybersecurity tip: If you get an email or text message about a package delivery containing links or asking for additional information, double-check that the order number matches the one in the confirmation email you received when you first purchased the item.
In catfishing scams, fraudsters create fake profiles on social media or dating platforms to trick people into sending them money or personal information. They often use attractive photos and send messages claiming they want a genuine relationship.
Once the scammer forms a bond, they may ask for money to cover travel expenses or bring up some heartwrenching story like having a sick family member with unpaid medical bills. In other cases, they send malicious links to infect the victim’s device with malware. Catfishers often request payment in the form of gift cards, since they’re hard to trace.
One distressing example of a catfishing scam is the “Keanu Reeves Scam.” A Colorado woman was tricked into believing she was romantically involved with the actor, sending over $5,000 in gift cards after the scammer showed her fake documents and promised lavish trips. Despite the actor’s representatives confirming he has no social media, she still believes it was the real Keanu Reeves.
Cybersecurity tip: A red flag that you may be dealing with a catfisher is if the individual refuses to connect with you via video chat or meet in person. Another warning sign is if they invent a sob story to try to convince you to send them money or gift cards.
Pretexting is a social engineering tactic in which a scammer impersonates a trusted source, such as your boss or a recruiter, to create a fake scenario and gain access to personal information.
For example, in a job scam, a cybercriminal might notice that you’re “open to work” on LinkedIn and pose as a representative of a company that matches your profile. They may inform you that you've been hired, but they need your Social Security number before you can start.
Once you provide your personal information, the supposed company representative disappears.
Cybersecurity tip: Legitimate employers will almost certainly never offer you a job without an interview. If you receive a suspicious job offer, contact the company directly through their official website to verify its authenticity.
Scareware is a type of social engineering scam that uses fear to trick people into downloading malware, sending money, or giving away personal information. It often starts with a pop-up message or phishing email claiming a virus has been detected on your device.
The message then urges you to download (fake) antivirus software or pay a fee to fix a non-existent issue. In many cases, the software steals your information or infects your device with malware.
Be cautious of any pop-ups from antivirus software not installed on your device as they’re most likely a scam. A legitimate antivirus will notify you of issues within their app, not through pop-ups in a browser.
Cybersecurity tip: Investing in real anti-virus software can help prevent malicious pop-ups, reducing your risk of falling for a scareware scam.
In watering hole attacks, cybercriminals target websites frequently visited by a specific group, like employees of a company, to infect their devices with malware or steal sensitive data. The attackers compromise the website by embedding malicious code, which then infects visitors’ devices. A watering hole attack can also use spoofed websites that mimic trusted ones.
One real-life example of a watering hole attack occurred between November 2023 and July 2024, when the Russian-linked APT29 group compromised Mongolian government websites. The attackers injected malicious code into these sites, exploiting vulnerabilities in Apple iOS and Google Android. Their campaign specifically targeted unpatched devices, allowing the scammers to steal sensitive information from visitors.
Cybersecurity tip: Avoid using company devices for personal activities. Only visit trusted websites related to work, and don’t browse unfamiliar sites on work devices. Always check a website’s URL carefully because a spoofed site can look very similar.
A quid pro quo attack is a social engineering scam where the attacker offers something in exchange for sensitive information or access to a system.
For example, the attacker might pose as a technical support agent, in return for the victim providing login credentials or other personal information. The goal is to exploit the target’s willingness to accept help or reciprocate, so the social engineer gains unauthorized access or valuable information.
Cybersecurity tip: Be cautious of unsolicited offers, especially if they require you to provide personal information or access to your accounts or device in exchange for help.
AI deepfake scams use artificial intelligence to create fake videos and audio recordings of real people.
Once the AI has enough data from video and audio recordings, it can generate highly realistic videos and voice clips in which people appear to say or do things they never actually did. Scammers use these AI scams to manipulate victims into taking actions like donating money, sharing sensitive information, or clicking malicious links.
In one example, the British engineering firm Arup lost $25 million after scammers used AI-generated deepfake messages to impersonate the company’s CFO. The scammer arranged a video call with an employee, convincing them to transfer large sums of money to bank accounts in Hong Kong. The fraud wasn’t discovered until after the transactions were completed, underlining the significant threat of deepfake scams in business environments.
Cybersecurity tip: Always be skeptical of videos and voice clips where a colleague or celebrity makes an unusual request. Contact your colleague via a different channel or look up a celebrity’s official social page or website if you’re planning on donating money.
Although cybercriminals are skilled at hiding their true intentions, most scams share a few common traits that make them easy to spot. Keep your eyes peeled for the following signs of a social engineering attack.
If you fall for a social engineering attack, take the following steps to protect your personal information:
Awareness of common social engineering schemes can help protect you, but scammers will never stop trying to get their hands on your information. For additional security, subscribe to LifeLock.
Our robust identity-protection suite includes powerful features like Privacy Monitor, which helps reduce the public exposure of your personal information, and Dark Web Monitoring, which patrols the murkier corners of the internet and notifies you if it finds your information has been exposed.
And if you do fall for a scam, our U.S.-based Personal Restoration Specialists can help you restore your identity and potentially reimburse you up to $25,000.
Phishing attacks are the most common type of social engineering. Nearly nine million phishing attacks were detected around the world in 2023.
Social engineering is a broad term that refers to the practice of manipulating or deceiving individuals into disclosing confidential data or performing actions that benefit the attacker. Phishing, a narrower term, is a type of social engineering where cybercriminals request sensitive data or send dangerous links disguised as legitimate messages, often via email.
A social engineer is someone who manipulates people into revealing confidential information or performing actions that compromise security, often by exploiting trust, emotions, or social norms.
Yes, social engineering attacks can happen offline. For example, a scammer might gain physical access to a workplace by convincing a security guard that they “left their badge at home” or simply tailgating an employee through security doors.
* Reimbursement and expense compensation varies according to plan. See policy terms, conditions, and exclusions at: GenDigital.com/legal. Stolen funds resulting from reasons other than identity theft, including voluntary transfers to scammers or disclosure of account data, are not eligible for reimbursement. More details here.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.