Hackers might try to strongarm their way into your online accounts to access private information, steal money, or scam people who trust you. In other cases, attackers just break in to troll you or steal your paid services. Regardless, recovering from account takeover fraud can be a major headache. Read on to learn tips and tricks on how to lock down your accounts and protect your personal information.
What is an account takeover (ATO)?
An account takeover happens when a cybercriminal uses stolen login credentials to access someone else’s account without authorization. Once they gain access, the attacker can exploit the account to commit identity theft, financial fraud, and other crimes.
The account takeover process involves an attacker:
- Accessing stolen login credentials.
- Testing the login credentials.
- Gaining access to their target’s account(s).
- Locking the owner out of the account(s).
- Stealing information, money, or services.
- Using the login details for as long as possible.
How do account takeovers happen?
To take over your account, a hacker needs to find a way to get into your account. They usually do this by exploiting system vulnerabilities or human error. Here are several examples of ways hackers might try to steal your login information:
- Brute force attacks: These attacks require hackers to try thousands of passwords until they find the right combination. You can fight brute force attacks by using two-factor authentication (2FA), which helps keep cybercriminals out even if they stumble on your password.
- Credential stuffing: This method allows hackers to easily use login credentials that were previously leaked in a data breach. You can protect yourself from credential stuffing by setting up data breach alerts that tell you when you’re compromised and if you need to reset your passwords.
- Packet sniffing: Sniffers are hackers who intercept and analyze unencrypted network traffic to sneakily steal login credentials. To protect yourself from packet sniffing, use a mobile VPN to protect your sessions, especially if you’re connecting to guest Wi-Fi.
- Phishing: This attack occurs when hackers trick users into clicking a link that allows them to capture login information or plant malware on the target’s device. Protect yourself from phishing attacks by never clicking on links from unknown senders.
- Man-in-the-middle attacks: When hackers intercept messages as they’re being sent to capture sensitive information like login information, it’s called a man-in-the-middle attack (MITM). Use secure messaging platforms and a mobile VPN to protect yourself from MITM attacks.
- Social engineering: This hacking scheme requires hackers to devise a believable ruse to trick their targets into willingly sharing their login information. Avoid social engineering schemes by verifying information and following protocols.
Once the hacker has your account information, it’s just a matter of testing the login credentials and leveraging them to steal or access other high-value accounts.
Who do hackers target in ATO attacks?
Hackers will try to take over any account that helps them meet their goals. This means hackers can attack you regardless of your income, job, or other factors. In many cases, it’s more useful to understand the types of accounts a hacker might try to break into and why.
Here are some examples of accounts that may be the target of an ATO attack:
- Bank accounts: Hackers often break into financial accounts to steal money and personal identifying information.
- Cloud storage accounts: Hackers may try to steal proprietary data or media from online file-storing systems.
- Customer accounts: Hackers may try to redeem the freebies, loyalty points, and frequent flyer miles you’ve earned over the years.
- Email accounts: Hackers sometimes break in and use your email for identity theft or to log into other accounts.
- Gaming accounts: Hackers may try to steal virtual currency, rewards, or loot from your video game accounts.
- Government accounts: Hackers sometimes target these accounts to re-route benefits like Social Security, SNAP, disability checks, or health insurance to themselves.
- Music and video streaming services: Hackers take over accounts like these so they can access the services they want without paying subscription fees.
- Social media accounts: These accounts are common targets because they allow hackers to secure blackmail leverage, spread misinformation, access other online accounts, or scam your followers. Learn more about how to protect against social media identity theft.
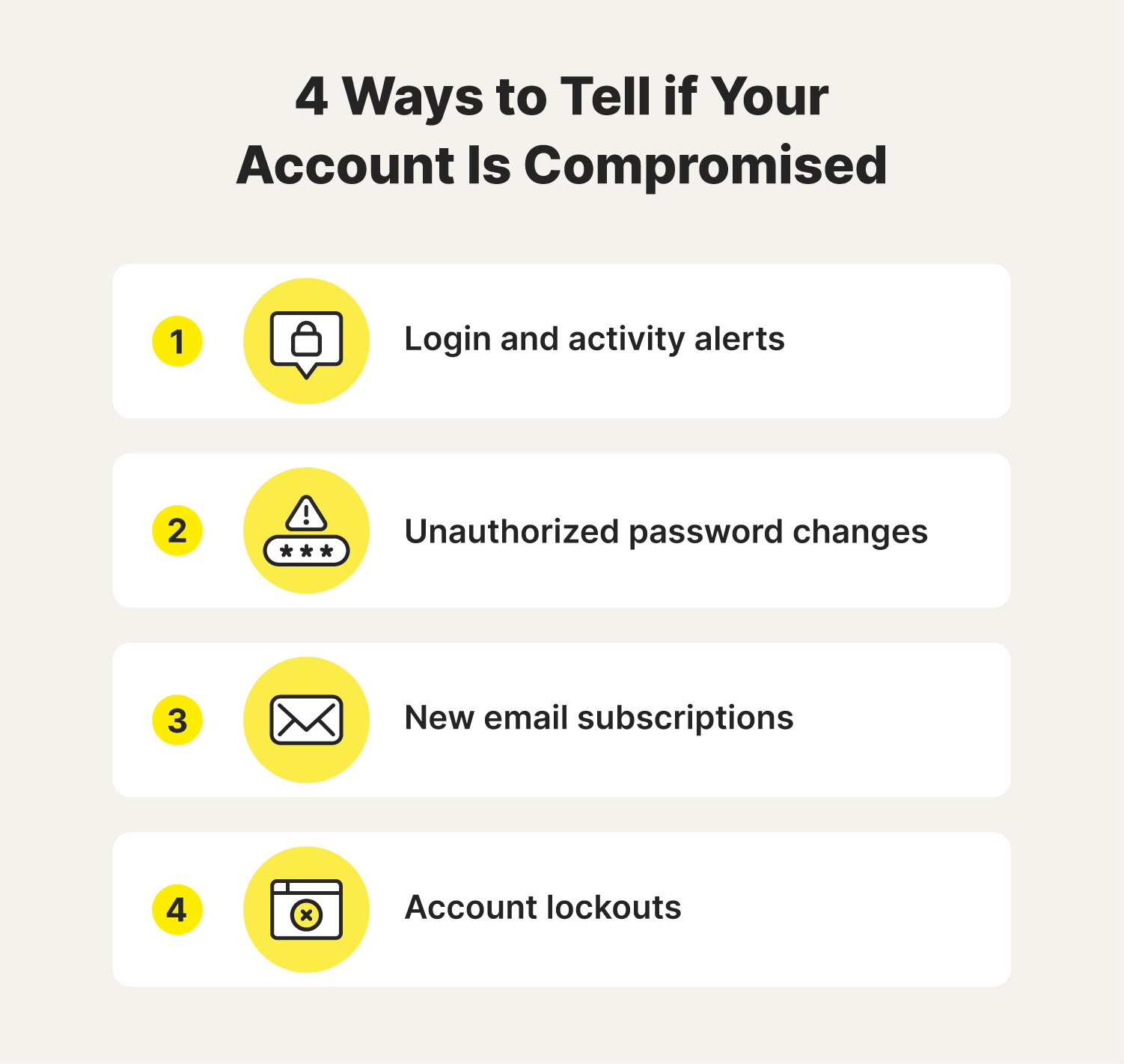
How to identify account takeover fraud
Account takeover warning signs will vary based on the platform and the hacker’s end game. But there are a few common signs you can look out for:
- Unusual login and activity alerts: These can signal that someone has illegally accessed your account.
- Unauthorized password changes: Password updates you didn’t approve are a clear sign that someone is trying to access your account and maybe even keep you out of it.
- Upticks in odd emails and subscriptions: Spam emails like this can indicate that someone is actively using your account or manipulating account settings.
- Unexplained account lockouts and deactivations: Being totally locked out is a major red flag that means someone has accessed your account and taken ownership.
How to prevent account takeovers
Account takeover prevention doesn’t have to be hard. You can do a lot to protect yourself by taking proactive steps to protect your accounts and devices. Here are a few strategies you can try to help prevent account takeovers:
- Set secure passwords: Make it harder for attackers to crack your credentials through brute force by setting strong and unique passwords.
- Choose hard-to-guess security questions: Keep attackers from bypassing the security measures by coming up with answers to security questions that no one else knows.
- Use a Web Application Firewall (WAF): Invest in tools that help identify and block malicious traffic and enhance overall account security.
- Enable two-factor authentication: Add an extra layer of verification beyond passwords, making it more challenging for unauthorized users to get in.
- Invest in an identity theft protection tool: Services like LifeLock Total can help by offering advanced identity theft protection, real-time credit monitoring, and alerts for unauthorized change attempts on financial accounts.
5 tips to recover from an account takeover
Account takeover recovery can be as simple as changing your password in some cases. However, it can get trickier if the attacker manages to steal money or personal information. Here are five tips to accurately assess the situation and recover your account:
- Run a malware scan: Use malware detection software to identify and remove malicious software on your device that may feed the attacker sensitive information.
- Report the compromised account: Report account takeovers to your service provider so they can investigate and help with recovery. Depending on the damages, you might also want to loop in local law enforcement.
- Change your passwords: Update your passwords and remove any unfamiliar devices from your account after a takeover.
- Review account settings: Look for vulnerabilities and increase your security settings.
- Monitor your financial accounts: Keep tabs on your credit report to catch and address financial fraud before the attacker can negatively impact your financial well-being.
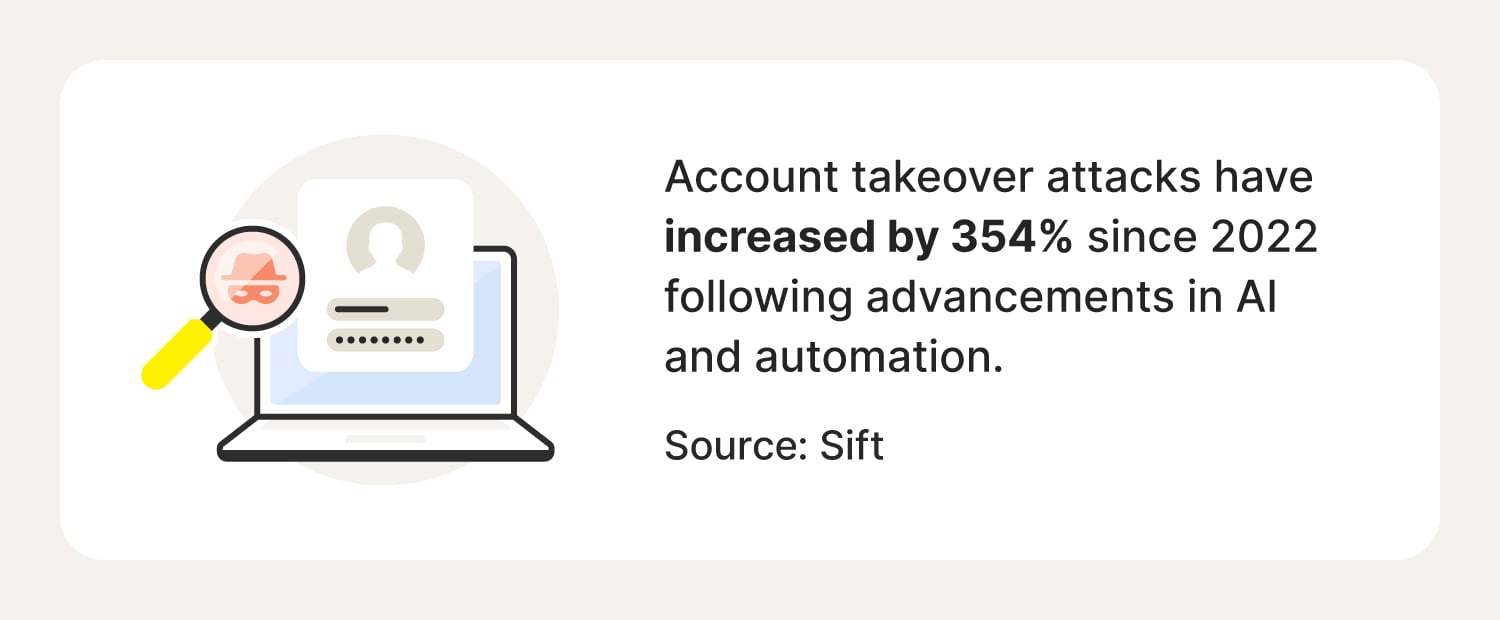
Examples of real-world account takeover attacks
People in the U.S. have lost billions of dollars because of account takeovers in recent years, and attacks continue to mount. That’s why it’s more important than ever to take control of your online security and be aware of the Cyber Safety measures the services you use have in place.
Here are just a couple of examples of companies that experienced data breaches and account takeovers in recent years because of poor training and cybersecurity measures.
Robinhood
Unauthorized users accessed about 40,000 Robinhood user accounts between 2020 and 2022. This happened after a scammer successfully tricked a customer service agent into helping them access customer support systems through social engineering, allowing them to find a foothold. Because the trading platform hadn’t implemented standard safeguards like encryption or multi-factor authentication, thousands of people were exposed to the threat of financial loss, and the company was ordered to pay $20 million in damages.
- Cyber Safety tip: Regularly review and update your account passwords, and consider using a secure password manager to generate and store complex, unique passwords for each of your financial accounts.
Zoom
In 2021, more than half a million Zoom users were affected by account takeovers after a cybercriminal posted employee login credentials on the dark web. Because of this, hackers started joining company meetings uninvited and posting inappropriate, sometimes damaging, content.
- Cyber Safety tip: Ask employees to set up two-factor authentication to keep hackers out of their accounts even if their information is stolen.
Invest in account takeover protection
With account takeovers on the rise, you can’t afford to leave your online safety up to chance. Invest in identity theft protection like LifeLock Total that can help with social media monitoring, financial account monitoring, savings account activity alerts, and data breach notifications.
FAQs about account takeovers
Still have questions about account takeovers? Here’s what you need to know.
How can I check to see if my account is secure?
Depending on the platform, you can typically go to the settings and see what devices have logged into your account and from where. If you’re unsure, visit the platform’s website to talk to a customer service representative or read a help center article.
How long does it take to recover from an account takeover?
The time it takes to recover from an account takeover mostly depends on how much information was compromised and the service provider’s recovery protocol. In the end, recovering can take a day to a few months.
What tools can I use to help prevent account takeovers?
You can help protect yourself against account takeovers by using tools like password managers and two-factor authentication.
What types of accounts are most susceptible to takeovers?
Accounts with weak passwords and limited security measures are at a higher risk for takeovers. Attackers might also be more likely to hack your accounts if the payoff is high (e.g., they expect you to have valuable information or a lot of money).
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- What is an account takeover (ATO)?
- How do account takeovers happen?
- Who do hackers target in ATO attacks?
- How to identify account takeover fraud
- How to prevent account takeovers
- 5 tips to recover from an account takeover
- Examples of real-world account takeover attacks
- Zoom
- Invest in account takeover protection
- FAQs about account takeovers
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
-and-prevention-tips-hero.jpg)