If you're like most U.S. adults, you have at least one credit card in your wallet. They’re a convenient way to pay, but they also expose you to risk, with nearly 60% of credit card holders reportedly experiencing some form of attempted fraud in 2023.
Among these threats is carding, a type of fraud used by cybercriminals to profit from stolen credit card information.
What is carding?
Carding is a type of credit card fraud where criminals, known as “carders,” use stolen credit or debit card information to buy gift cards or prepaid cards, which they then resell for profit. This strategy is favored over direct fraudulent purchases because it makes tracking carders much more difficult.
Carding fraud is often just one component of much larger data fraud, identity theft, and money laundering operations run by organized crime gangs.
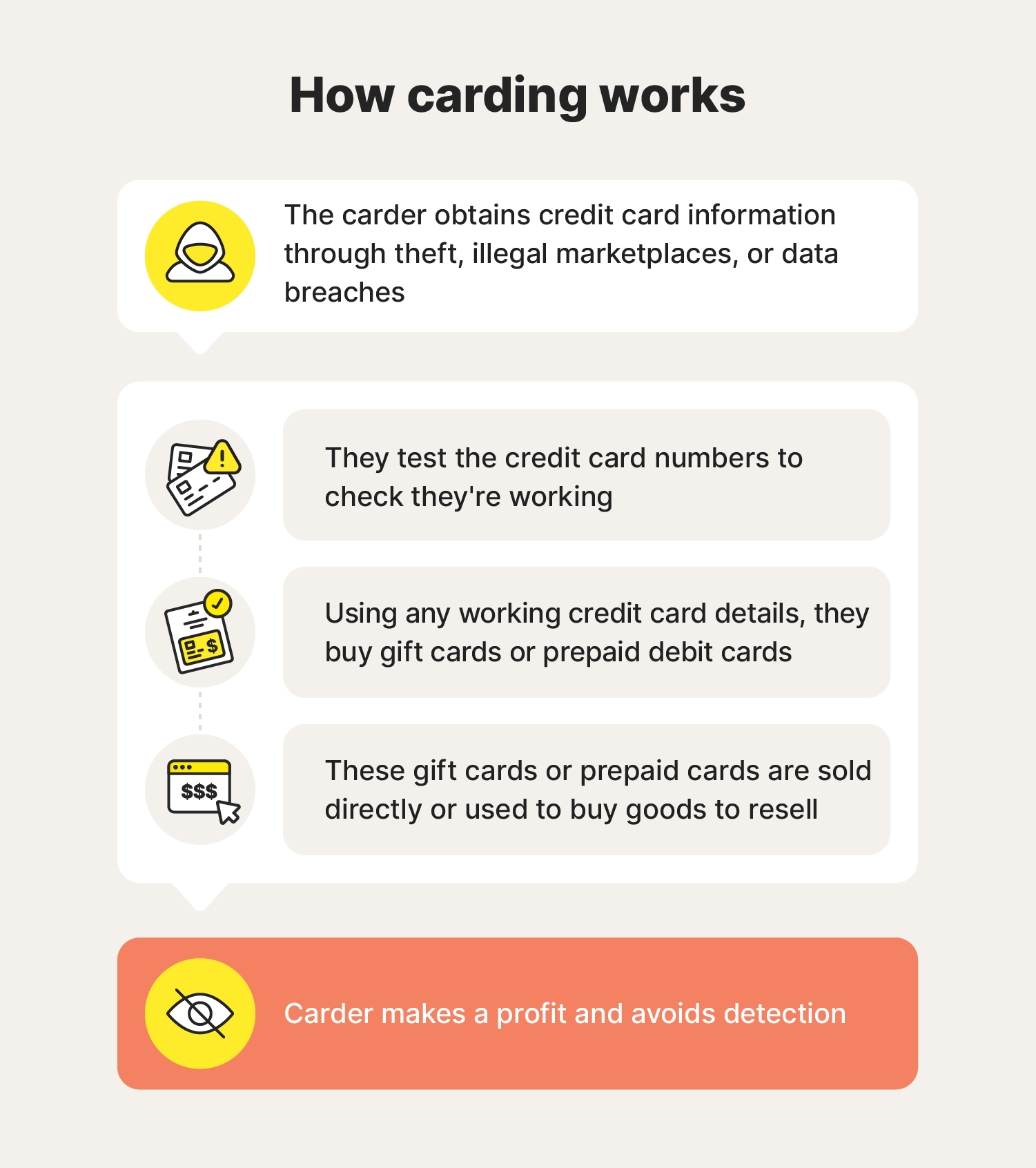
How does carding work?
Carding schemes typically involve fraudsters illegally obtaining card details, checking the card is active by attempting small transactions, purchasing hard-to-track prepaid cards with valid stolen details, and then selling the prepaid cards for profit.
Sometimes, carders collaborate with “cashers,” who act as middlemen by purchasing stolen credentials and then monetizing themselves. This reduces carders' risk of being caught and makes it even more difficult to trace carding operations.
Here’s a breakdown of each step in the process:
1. Stealing card information
Carders use various methods to steal debit or credit card numbers, including phishing scams, where victims are tricked into providing details via fake websites or emails; skimming devices placed on ATMs or card readers; and malware that captures data from compromised computers or phones.
2. Testing credit cards for validity
Once carders obtain credit card information, they test the credentials to ensure the cards haven’t been reported lost, stolen, or deactivated. Sophisticated carders may use “carding bots,” which are automated scripts that quickly test large volumes of cards in bulk.
Carders typically test cards by making small transactions — usually under $10 — on e-commerce sites. These low-value payments are less likely to be detected and flagged as fraud by the card owner.
3. Purchasing gift cards fraudulently
When they find card details that work, carders typically use them to purchase gift cards or prepaid debit cards. This makes their crime less traceable by minimizing the number of transactions they need to make on the stolen card, making it easier for them to get away with it.
4. Leveraging gift cards for profit
Once the criminal has purchased the gift cards or prepaid cards, they can either sell them for profit or use them to buy expensive items, like laptops and televisions, which can easily be resold for cash.

How do criminals get credit card information
Cybercriminals use a range of nefarious technological and social engineering techniques to steal credit card information. And, once obtained via malware, phishing, or card-skimming attacks, the data may be sold or shared with other crooks on so-called carding forums.
Here’s a closer look at the different methods carders use to harvest credit card details:
Malware
Malware can be used to steal credit card information by infecting devices to log keystrokes, intercept online transactions, or extract saved card details. Other forms of advanced spyware may even mimic legitimate payment gateways to collect sensitive personal information such as credit card numbers and account passwords.
Phishing
Phishing occurs when scammers contact people via text, email, or social media messages to impersonate trusted entities — such as banks or retailers — urging them to click malicious links or enter personal information such as card details on fraudulent sites. Phishing attacks were the most common type of cybercrime in 2023, with almost 300,000 complaints filed.
Carding forums
Carding forums are illegal dark web platforms where criminals can anonymously buy, sell, or trade stolen credit card information. These forums — as well as encrypted messaging apps like Telegram or WhatsApp — often host discussions on using fraudulent card data for purchases or withdrawals, bypassing security measures, generating fake cards, exploiting vulnerabilities, or laundering stolen funds.
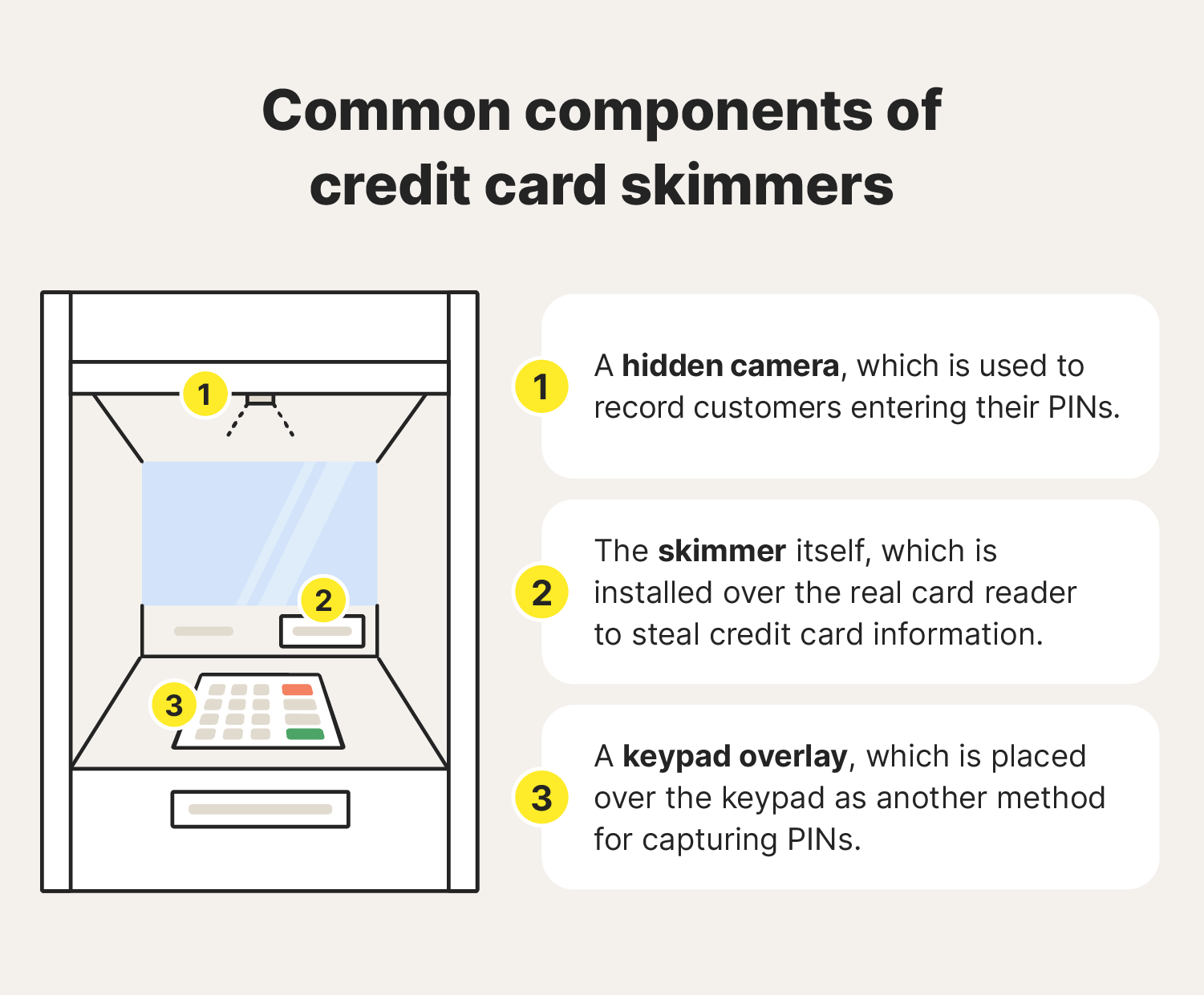
Credit card skimming
A credit card skimmer is a small device that thieves install on top of a legitimate credit card reader, like those in ATMs. If you insert your credit card or debit card into a compromised machine, the card skimmer may be able to read and store your card's information. Skimmers also often attempt to capture PIN numbers via a hidden camera or keypad overlay.

Hacking
Hackers may exploit software vulnerabilities or use brute force attacks to gain unauthorized access to devices and databases containing sensitive data. When they target businesses that process transactions, like ecommerce websites, they can steal or leak large volumes of customer information in a data breach.
Fake online stores
Some scammers create fake online stores that mimic legitimate e-commerce websites to trick people into entering their card information, believing they’re making a real purchase. These counterfeit sites often offer products at unusually low prices to lure shoppers, but fail to deliver the items and instead use the stolen information in a carding scheme.
Shoulder surfing
Shoulder surfing is a low-tech way for carders to steal card information by watching secretly as you enter your card details in a public place. This can happen at ATMs, point-of-sale terminals, or even while you shop online in a coffee shop.
How to avoid carding
To help avoid carding, use reliable anti-malware software to detect malware that could compromise your security, and ensure that your operating system and other software are kept up to date. Additionally, set up credit card notifications to track transactions in real time, helping you catch any unauthorized activity quickly.
Use the following strategies to help protect your credit card or debit card from carders:
- Use anti-malware software: Malware blocking and spyware detection tools can help you detect harmful programs that fraudsters use to steal your card details and remove them from your device.
- Promptly run software updates: Keep your devices up to date by downloading the latest operating system updates and software patches to maximize your protection against hackers.
- Learn to spot phishing attempts: Avoid clicking links or downloading attachments from scammers or unknown senders, and verify any suspicious messages claiming to be a trusted party through official channels.
- Sign up for credit card notifications: Consider enabling transaction alerts on your credit or debit cards to catch fraudulent charges quickly.
- Check website domain names: Fake website domains often contain unusual spelling or capitalization. Before making any purchases or providing credit card information, always check you’re on the official website, and not a fraudulent copy.
- Invest in dark web monitoring: Dark web monitoring tools can scan the dark web for your credit card details or personal information, helping you take action to protect yourself from potential carding attempts.
- Be cautious when using ATMs: To identify a card skimmer on an ATM, look for loose or misaligned card readers or unusual overlays. If anything seems suspicious, avoid using the machine and report it to the bank.
- Practice good cybersecurity practices: Follow cybersecurity best practices by using strong, unique passwords, enabling two-factor authentication, and avoiding clicking suspicious links in emails or texts.
How businesses prevent carding fraud
To protect themselves and their customers, online retailers implement an array of security measures designed to help prevent data leaks and unauthorized transactions. They include:
- Multifactor authentication (MFA): MFA adds account security by requiring multiple verification steps to log in, making it harder for carders to access accounts with stolen login information.
- CAPTCHA: CAPTCHA tests block scripts by verifying users are human, preventing carders from using bots to test large numbers of stolen cards.
- Address verification system (AVS): AVS checks the billing address entered at checkout against the card issuer’s records to flag mismatches.
- Card verification value (CVV): The CVV number is a three- or four-digit security code on credit cards that verifies the buyer has the physical card, helping prevent fraud with stolen card numbers.
- Velocity checks: Some merchants monitor transaction speed and volume to detect unusual patterns that might indicate fraud.
- Authorization/capture: Merchants authorize small charges before finalizing transactions, allowing time to identify potential fraud.
- Payer authentication systems: These systems verify your identity at checkout by comparing transaction data with your credit card provider's records.
But despite all this, “card-not-present” fraud, where cybercriminals use stolen card information for unauthorized online purchases, accounted for 73% of all card payment fraud in 2024, resulting in more than $10 billion in losses.
What to do if you experience a carding attack
If you think somebody has used your information in a carding attack or attempted to get access to your card details, take the following steps to help protect your financial well-being:
- Notify your credit card issuer of fraudulent activity: If you notice unfamiliar charges on your card, contact your credit card issuer immediately online or by phone to report fraudulent activity.
- File a report with the FTC: Visit IdentityTheft.gov to report the fraud attempt and get a recovery plan that can help minimize the impact of a carding attack.
- Invest in identity theft protection: Identity theft protection tools like LifeLock, which monitors millions of data points, can track where your information appears online and flag unauthorized use of your personal details, helping you protect against carding and other forms of fraud.
Under the Fair Credit Billing Act, cardholders are liable for no more than $50 in unauthorized charges, meaning the direct financial impact of falling victim to a carding scheme is unlikely to be significant.
But disputing fraudulent charges is a hassle, and carding can have other impacts including negatively affecting your credit score, so it's important to take steps to protect yourself.
Protect against carding and other fraud
Understanding how carding works is a good first step toward protecting your finances, but it’s just the start.
Subscribing to LifeLock adds an extra layer of protection against fraudulent activity, with features including dark web and credit monitoring, automatic alerts of potential identity theft, and stolen wallet protection that helps you take action to reduce your vulnerability if your wallet is stolen.
FAQs
How can I tell if my credit card information has been compromised?
The most reliable indicators of carding are unfamiliar or unauthorized transactions appearing in your online banking app or on your monthly card statements. In particular, look out for:
- Multiple small charges
- Charges from an unknown merchant
- Payments from overseas
- Declined transactions
- Decreased credit availability
Can carding impact my credit score?
If you fall victim to a carding scheme, you might see a negative impact on your credit score based on changes to your credit utilization ratio and potential missed payments on fraudulent purchases. However, catching and stopping carding attacks early may enable you to resolve the situation before it has downstream effects on your credit score.
Is carding illegal?
Yes, carding is illegal. It involves using stolen credit card information for fraudulent purchases, which makes it an example of both identity theft and financial fraud, both of which can carry serious legal consequences.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.







