1 Identity Lock cannot prevent all account takeovers, unauthorized account openings, or stop all credit file inquiries. The credit lock on your TransUnion credit file and the Payday Loan Lock will be unlocked if your subscription is downgraded or canceled.
Credential stuffing affects millions of consumers each year, leading to data breaches and compromised accounts. In 2023, personal genomics company 23andMe reported that 14,000 user accounts were breached after another company's data leak exposed reused passwords. The attack revealed sensitive information such as display names, genetic ancestry, and locations of nearly 7 million people.
Thankfully, there are steps you can take to protect yourself from credential stuffing attacks. Keep reading to discover how credential stuffing works, and, more importantly, how to safeguard your personal information with practical, proactive measures.
What is credential stuffing and how does it work?
Credential stuffing (also called password stuffing) is a cyberattack in which hackers use stolen username and password combinations to brute force their way into user accounts.
Usually, attackers obtain leaked credentials after data leaks. Because online users often reuse passwords for multiple accounts (an account privacy no-no), attackers can then run automated tools to test large lists of compromised usernames and passwords until they find another account using matching credentials.
Once they gain account access, they can steal personal information, make fraudulent purchases, or sell account details on the dark web.
Credential stuffing vs. brute force attack
Credential stuffing is technically a type of brute force attack. But, the biggest difference is that credential stuffing uses known username-password pairs gleaned from data breaches to target accounts, while brute force attacks blindly guess passwords through random combinations until they’re successful.
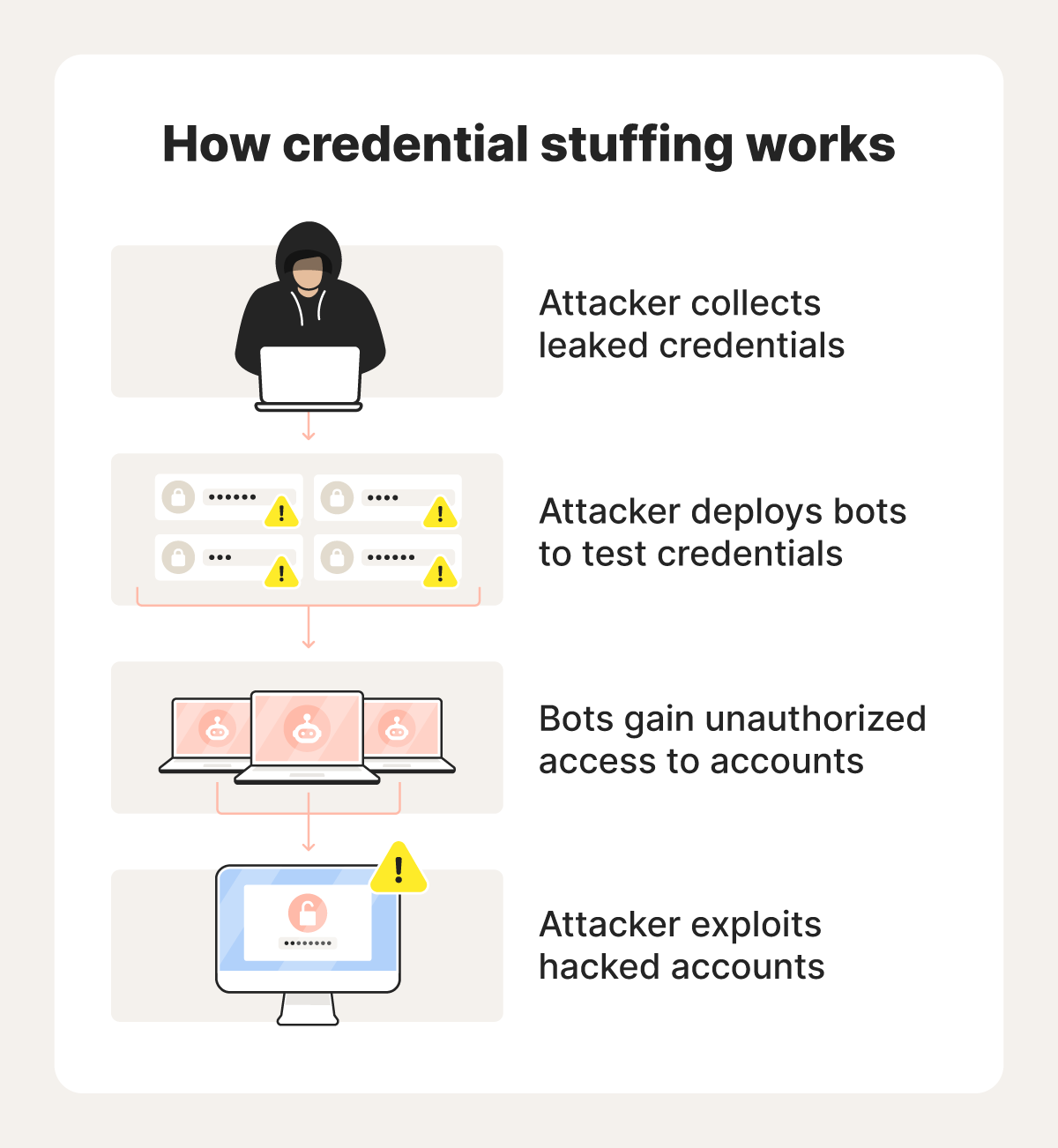
How credential stuffing works
Credential stuffing works by using bots (automated software programs designed to perform repetitive tasks) to test stolen credentials, helping cybercriminals gain unauthorized access to accounts so they can exploit the account user's personal information.
Here's a step-by-step look at the credential stuffing process:
1. Attacker obtains stolen credentials
The first step in credential stuffing is for the attacker to obtain stolen account credentials. These credentials can come from several sources:
- Data breaches: A data breach occurs when attackers exploit security flaws to access sensitive information like usernames and passwords. This stolen data can be used for identity theft or account takeovers.
- Data leaks: Unsecured platforms or incidents that unintentionally expose personal information can lead to leaked credentials, which attackers can access and use.
- Dark web marketplaces: Attackers frequently buy and sell stolen credentials on dark web marketplaces, which are hidden online platforms that facilitate the exchange of goods, including stolen data and other illegal goods.
- Phishing attacks: In phishing attacks, attackers trick individuals into providing their login details by masquerading as legitimate entities, giving them access to personal credentials.
2. Attacker uses bots to test stolen credentials
Once the attacker gains access to a list of stolen usernames, passwords, or both, they deploy bots to automatically test these credentials across various websites. To prevent being blocked for excessive failed login attempts or other suspicious activity, these bots can conceal their IP addresses, evading detection.
3. Attacker gains unauthorized access to accounts
When the bots find a match, the attacker gains unauthorized access to the target’s account and proceeds with the account takeover. Networks of infected devices controlled by attackers (botnets) can launch thousands of login attempts in seconds, making it easy to exploit unsecured or weakly secured accounts.
Attackers target many types of accounts, including:
- Email accounts: Attackers target email accounts because they often contain personal information, receive password reset or verification emails for other accounts, and are a gateway to further hacking attempts.
- Social media profiles: Social media accounts are often targeted to steal personal information, impersonate users, or leverage the accounts for malicious purposes, such as targeting friends’ lists with phishing attacks.
- Business or employee accounts: Hackers target these accounts to access sensitive company information in business email compromise attacks (BEC attacks), steal proprietary data, or launch further attacks on the organization's network.
- Online banking and shopping accounts: Hackers target these accounts to steal credit card information or verify fraudulent transactions. Subscribing to LifeLock Total can help protect these accounts by providing alerts for new bank account applications and attempts to take over existing accounts.1
4. Attacker exploits accounts
If the attacker gains access to one of your accounts, they can exploit it for malicious purposes, like stealing personal details, making fraudulent purchases, or selling account details on the dark web. They may also lock you out or use the account to launch further attacks.

Why is credential stuffing effective?
Credential stuffing is a highly effective tactic for hackers because it exploits the common habit of reusing login credentials across multiple platforms. When a username and password from one breach are exposed, cybercriminals can easily use them to gain unauthorized access to other accounts. And research consistently shows that this tactic is successful.
A recent survey commissioned by Forbes Advisor shows that 46% of Americans reported their password was stolen within the last year. Of those respondents, 30% believe it was due to recycling passwords across platforms.
Other attributes that contribute to credential stuffing's success include:
- Detection difficulty: Credential stuffing attacks are hard to detect because they largely mimic legitimate user behavior, making it difficult for traditional security measures to identify the attack.
- Low barrier to entry: The cost and technical skill needed to launch a credential stuffing attack are minimal. For as little as $40, attackers can buy stolen banking login credentials and use automation tools to carry out the attack.
- Easily attainable credentials: Nearly 10 billion plaintext passwords were discovered on an online forum in July 2024 due to the “rockyou2024.txt” data leak, highlighting the importance of protecting your personal data, which starts by using unique passwords online.
- Automation tools: Credential stuffing attacks rely on bots and other automated tools to quickly test large sets of credentials across multiple platforms, allowing attackers to bypass security measures that would otherwise block manual login attempts.
Real-world credential stuffing attacks
Since it's relatively easy for cybercriminals to access personal data online, credential stuffing attacks are a persistent threat. Here are a few recent, real-world examples that impacted large companies and their customers:
- Roku: In 2024, Roku experienced two credential stuffing attacks that affected nearly 600,000 customer accounts. Hackers used stolen login credentials from unrelated sources to gain access, making unauthorized purchases in around 400 accounts. Roku responded by resetting passwords, reversing fraudulent charges, and enabling two-factor authentication (2FA) for added security.
- Okta: In 2024, Okta detected a credential stuffing attack that targeted endpoints that support its cross-origin authentication feature. Cybercriminals attempted to access multiple endpoints using compromised login credentials, affecting. In response, Okta provided mitigation guidance, including adopting passkeys for stronger security.
- PetSmart: PetSmart also experienced a credential stuffing attack in 2024 that targeted customer accounts using compromised login credentials from other sites. The company alerted affected customers and urged them to use unique passwords for each account to prevent similar attacks.
- Levi’s: On June 13, 2024, a credential stuffing attack impacted over 70,000 Levi’s site users. While attackers likely did not steal significant funds, the incident raised concerns about the misuse of personally identifiable information (PII) for follow-up phishing attacks, which prompted Levi's to advise users to reset passwords and review their account details for accuracy.
- PayPal: PayPal recently disclosed a credential stuffing attack that compromised around 35,000 customer accounts, which exposed sensitive data including names, Social Security numbers, and tax identification details. PayPal has since taken corrective actions, but the incident led to a $2 million settlement with New York State for failing to meet cybersecurity regulations.
How can I detect credential stuffing?
Credential stuffing attacks can be difficult to detect because they mimic legitimate login behavior, using real credentials just like you would when accessing your own account. However, there are a few warning signs that may indicate you're being targeted by such an attack.
Common signs of credential stuffing include:
- Unusual account activity
- Failed login attempt notifications
- Unauthorized purchases or account changes
- Alerts about logins on unknown devices
What should I do if I think I’m the victim of credential stuffing?
If you suspect you’ve been targeted by a credential stuffing attack, start by reviewing your account details to confirm that only your own email address and information are associated with the account. Then, change your password, ensuring it’s strong and unique to that specific site, and enable 2FA for an added layer of security.
Here are some more tips for protecting your personal information if you think you’re a victim of credential stuffing:
- Enable 2FA and update your passwords across all accounts, not just the one you believe may be compromised.
- Check for unusual activity like unauthorized purchases, suspicious login attempts, or changes to your account information.
- Monitor your financial accounts for unauthorized transactions, unusual charges, or changes in account balances.
- Contact law enforcement to file a report and help initiate an investigation and potentially prevent further harm.
- Invest in identity theft protection to receive alerts about large data breaches, and get personal information monitoring to keep track of fraudulent uses of your info.
How to prevent credential stuffing
The best way to reduce your vulnerability to credential stuffing attacks is to prevent your credentials from falling into the wrong hands to begin with. To safeguard your personal information and reduce your exposure, follow these key strategies:
- Use unique, strong passwords: Use unique passwords for all your accounts. All passwords should be between 12 and 16 random characters, making them more challenging to guess.
- Enable 2FA: Verify your identity using a second form of authentication, like a code sent to your phone or email, in addition to a password. This extra layer of security makes it much harder for attackers to access accounts — 99% harder, in fact — even if they have stolen login credentials.
- Use a password manager: A password manager helps generate and store complex, unique passwords for each account, reducing the risk of reusing passwords.
- Beware of phishing attempts: Avoid clicking links or opening attachments in unsolicited emails or texts. Attackers sometimes use phishing techniques to steal login credentials.
- Invest in data breach detection: If your email or other personal information has been compromised, a trusted breach detection tool can help you find out.
- Monitor your accounts regularly: Watch your account activity for unusual or unauthorized actions. Use notifications for logins and transactions to stay informed of suspicious activity, such as unusual login attempts.
Help protect your credentials with LifeLock
Credential stuffing attacks are more common — and destructive — than most people realize. Knowing how they work is the first step in defending yourself.
For stronger protection, get LifeLock Total. It offers powerful tools to help monitor for signs of identity theft, including the suspicious use of your personal information. You’ll also receive alerts about large-scale data breaches that may involve your credentials, giving you the chance to act quickly and reduce the risk of account takeovers.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- What is credential stuffing and how does it work?
- How credential stuffing works
- Why is credential stuffing effective?
- Real-world credential stuffing attacks
- How can I detect credential stuffing?
- What should I do if I think I’m the victim of credential stuffing?
- How to prevent credential stuffing
- Help protect your credentials with LifeLock
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.


-and-prevention-tips-thumb.jpg)



