†LifeLock does not monitor all transactions at all businesses. Credit reports, scores, and credit monitoring may require an additional verification process and credit services will be withheld until such process is complete.
Smishing attacks are deceptive communications that, like other forms of phishing, are performed by scammers masquerading as people you know or impersonating reputable agencies or businesses.
Understanding how smishing works, as well as knowing its hallmarks, can help you identify these malicious attacks. Keep reading to learn about the meaning of smishing, how smishing works, and examples of real-life smishing incidents. Then, discover tips on preventing smishing and safeguarding your personal information.
Smishing definition
Smishing (short for SMS phishing) is a type of cybersecurity attack in which scammers send fraudulent text messages to trick you into tapping malicious links, and revealing sensitive information such as passwords or credit card details. These attacks often employ manipulative social engineering tactics to spread malware or commit identity theft.
In most respects, the definitions of smishing and phishing are interchangeable—the only difference is that phishing encompasses all platforms and channels, whereas smishing relates specifically to SMS messages sent to mobile devices.
How does smishing work?
Smishing works by using fraudulent text messages to deceive individuals into tapping malicious links or revealing personal information. These messages are intended to prompt users to expose sensitive data, such as passwords or financial details—or otherwise compromise their own security—and allow scammers to commit financial or identity theft.
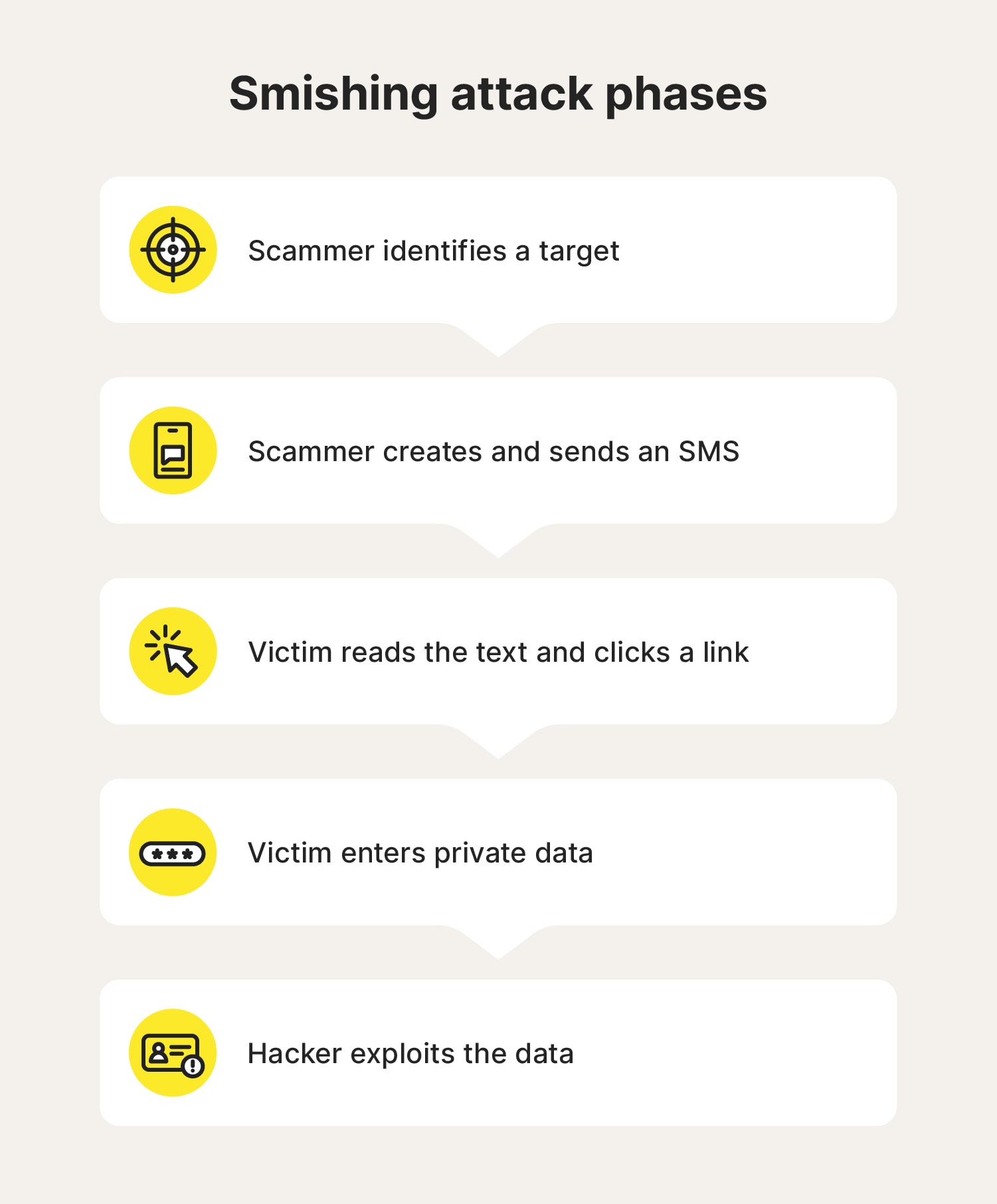
Here are the basic steps of a smishing attack:
- A target is identified: Scammers begin smishing attacks by identifying individuals to target, often using contact lists sourced from prior data breaches or gathered from publicly available databases.
- A message is created and sent: The attacker crafts a message intended to induce fear or urgency, prompting the recipient to tap a link that leads to a fake website or respond with personal information. The scammer often uses a spoofed number to send the SMS, making the text appear to originate from a reputable source.
- The victim engages: When the recipient opens the SMS, they encounter a call to action—typically prompting them to tap a link, enter personal information, or call a specific phone number.
- Data is provided and stolen: If the recipient falls for the ruse, the attacker captures the desired information, such as login credentials and banking details, or the data is harvested through malware.
- Stolen data is exploited: Once the attacker has the data, they can use it to steal the recipient’s identity, access their accounts, or make fraudulent purchases.

Types of smishing scams
Smishing scammers are constantly devising new techniques and tactics. But most schemes generally fall into one of several broad categories. Common types include phishing links to fake websites, urgent messages claiming account issues, prize notifications, and requests for verification codes.
These are the most popular types of smishing scams:
- Impersonation: A scammer pretends to be someone you know, or a reputable brand or institution.
- Tech support: Purporting to be part of a security or tech support team, the smisher says somebody hacked your account and that they need your personal information to fix it.
- Account suspension or password reset: You receive a text stating that your account has been suspended, urging you to tap a link or create a new password to reinstate it.
- Gift or prize: The message claims that you’ve won a prize or received a gift, asking you to provide information or tap a website link to claim it.
- Charity: Especially common during the holidays or after a newsworthy disaster, attackers pretend to be from a relief organization or charity and send text messages asking for donations.
- Tax scams: Smishing tax scams often impersonate CEOs or HR leaders seeking sensitive information like W-2s and banking details. Scammers can also masquerade as IRS reps, offering fake refunds and other benefits to steal personal data.
- Missed package: A smisher contacts you to say you’ve missed a package delivery and that you need to give them personal information or pay to schedule a new delivery.
- Fraud alert: You receive an SMS notification claiming you’ve been a victim of fraud, with an urgent prompt asking you to provide information or sign up for a service to prevent identity theft.
- Financial scam: These deceptive text messages impersonate banks or financial institutions, prompting recipients to share sensitive information or tap malicious links, which can result in identity theft or financial loss.
Real-world smishing attack examples
There are many different ways that identity theft can occur, and staying ahead of the bad guys can feel like an impossible task. But gaining an understanding of real-world examples of smishing scams can help you recognize and avoid potential threats.
Here are some specific instances of smishing attacks that illustrate the tactics smishers use and the potential impact on unsuspecting targets.
Example #1: IRS SMS scam
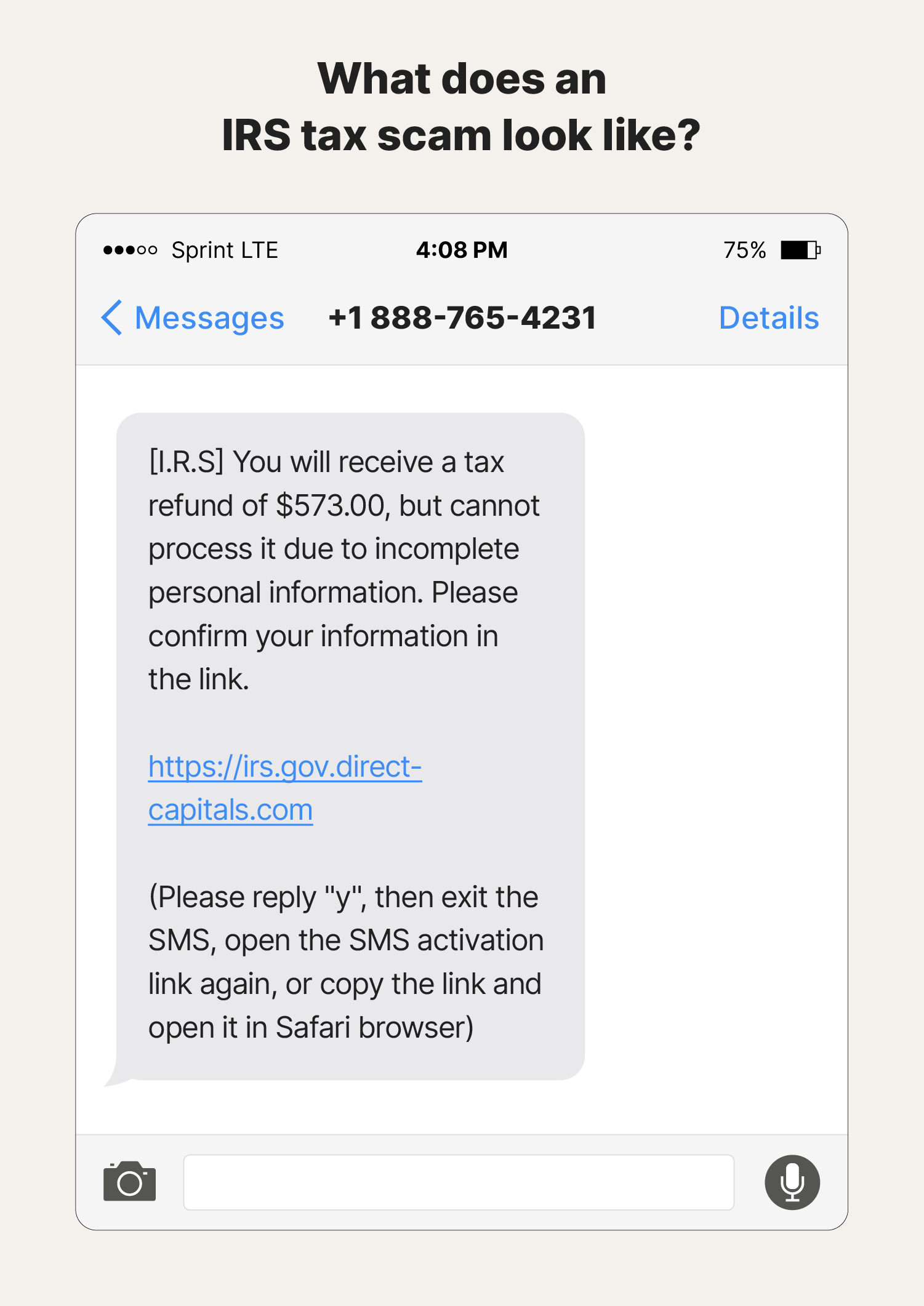

In this scam, a Reddit user received a text claiming they had a refund from the IRS and needed to tap a link to claim it. The link displayed "irs.gov," but the URL also included "direct-capitals.com." This additional info in the link raised alarm bells, prompting the recipient to avoid tapping it. If they had tapped, their banking details and personal information could have been compromised.
Example #2: USPS SMS scam
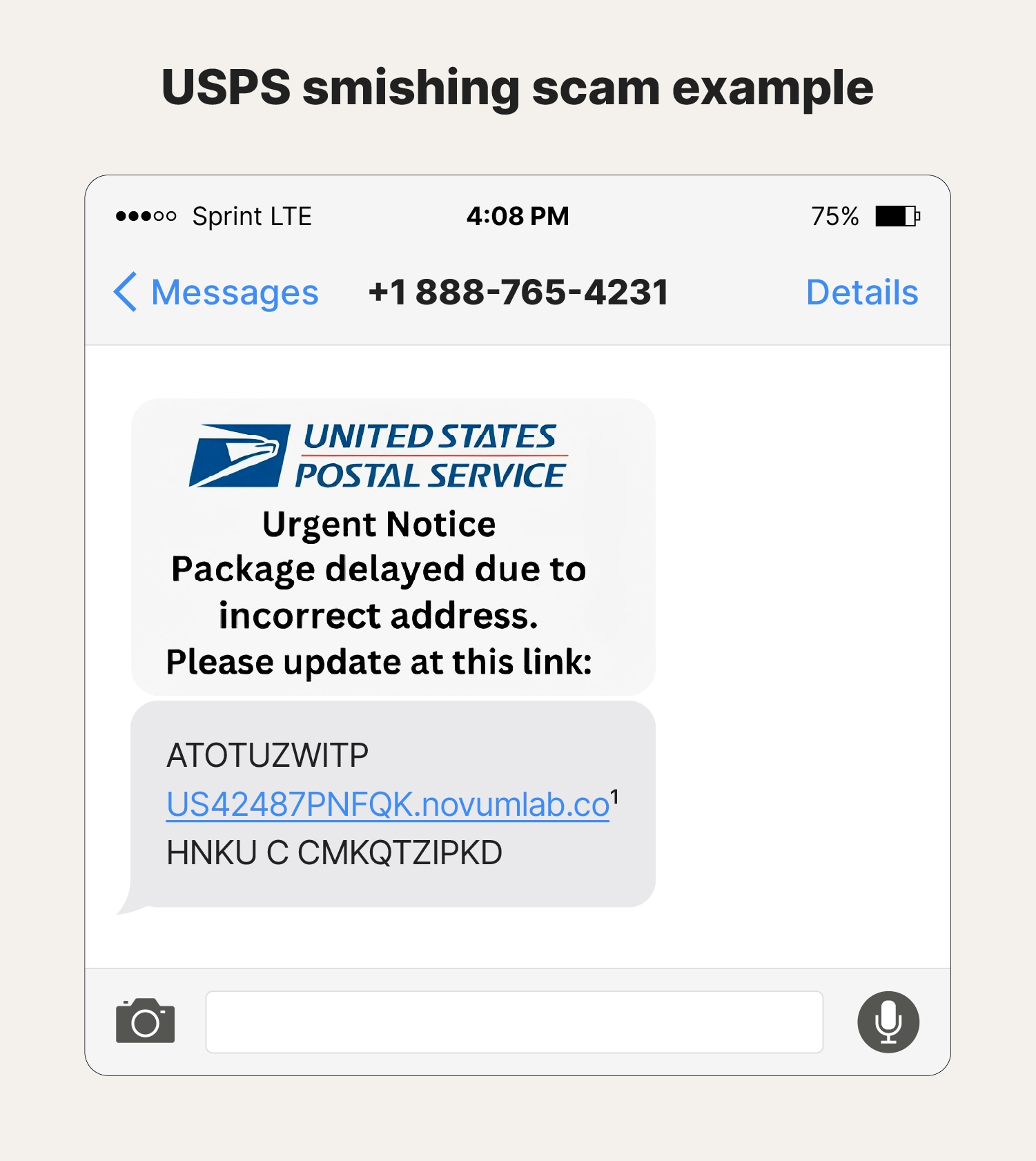

Package delivery smishing scams often pose as major delivery services like FedEx, UPS, and USPS. For instance, you may receive a text claiming to be from USPS, stating a package couldn’t be delivered due to an incorrect address. The scammer may urge you to tap a poorly formatted link to update your address. If tapped, you risk exposing personal information, such as your home address and phone number, which could be used to commit fraud.
Example #3: Toll SMS scam
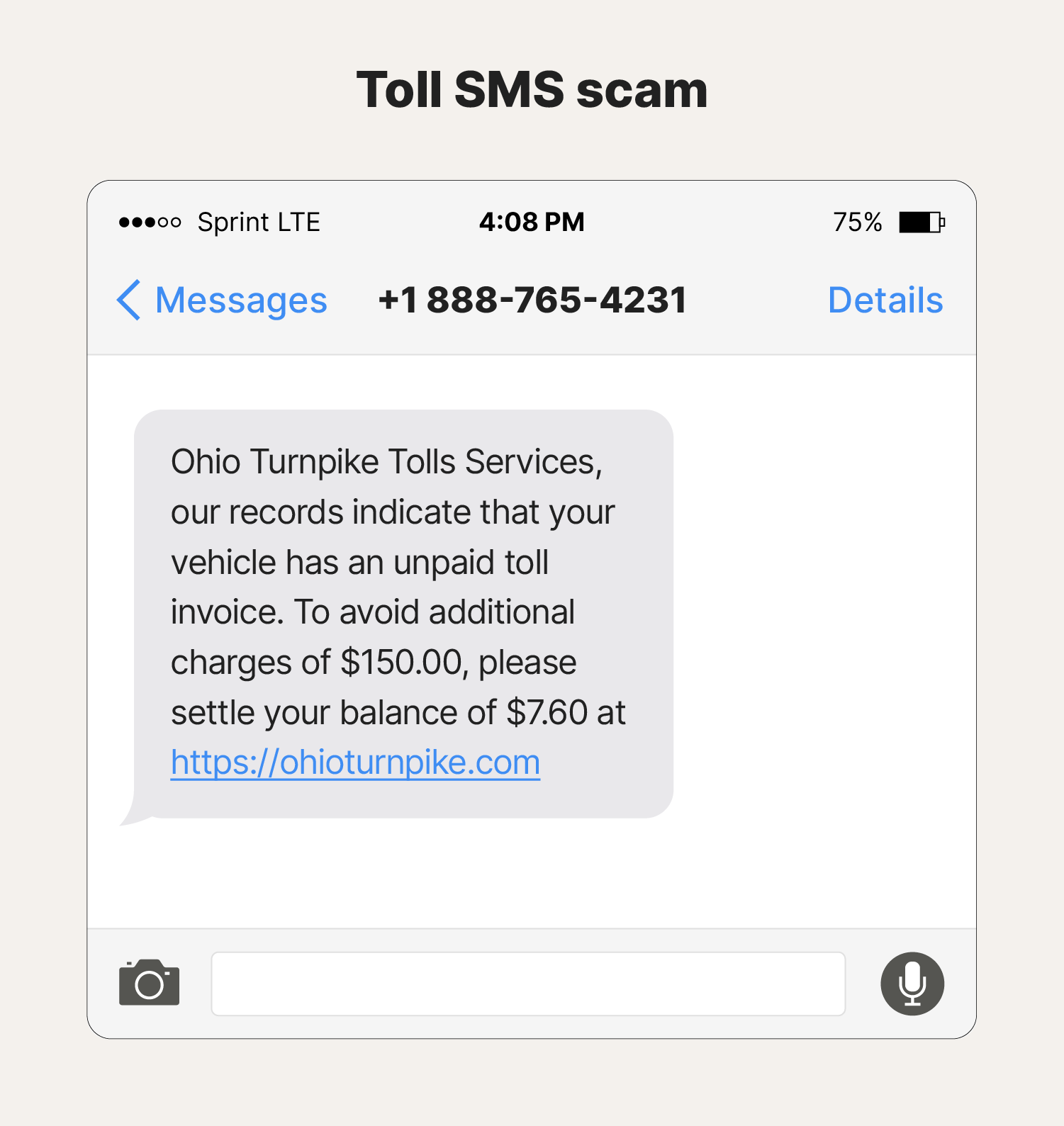

In this financial scam example, a recipient receives a smishing message regarding an unpaid toll. While the link looks very convincing, someone who uses the turnpike regularly (or researches the turnpike URL online) should know that the address ends in “.org” instead of “.com.” The scammer has created a fake website to steal money and payment information like credit card details.
6 ways to tell if a text message is real or a smishing attempt
Smishing attempts have become more prevalent and sophisticated, but watching out for key warning signs such as phone number irregularities and content quirks can help you identify potentially fraudulent messages.
To help avoid becoming a victim, be wary of these common indicators of smishing attempts:
- Unknown or unrecognized numbers: Scammers often withhold their caller ID, or use untraceable numbers to conceal their identity.
- Unusual phone numbers: Short phone numbers and out-of-area phone numbers can also be signs of scams.
- Irrelevant context: If you haven’t used the service or company the text is from, aren’t expecting a delivery, or haven’t entered a prize or lottery draw, the message is almost certainly a scam.
- Strange requests: Financial institutions and other legitimate organizations won’t ask for your personal information via text message. Any SMS you receive requesting private data is likely a scam.
- Grammar and spelling errors: Smishing attacks may come from abroad and often include misspelled words and poor grammar (although the availability of generative AI tools has made such mistakes less common).
- Fear-inducing language: Smishing attacks exploit fear to prompt immediate action without verification by demanding urgent responses that pressure you into sharing personal information.
How to help prevent smishing
To help prevent smishing and protect yourself against identity theft, be cautious of text messages requesting urgent actions, especially if they seem threatening, or—conversely—too good to be true. Use all available tools to safeguard your personal information and always verify the sender’s identity.
Here’s how to respond to smishing attacks and help prevent data theft:
- Be skeptical: Smishing exploits fear and urgency to prompt immediate action. Be cautious of messages requesting money or personal information, and take time to evaluate the situation before tapping links or sharing details.
- Verify the sender: Check a sender's number against online databases of known scam numbers, or on platforms like Reddit where users share details of smishing attempts.
- Impersonated numbers: Remember that attackers use spoofing tools to alter their phone numbers to appear official—never trust a text just because of the number. Contact the business directly via an official channel to confirm if they sent the message.
- Don’t download attachments or tap links: If you are at all suspicious about the veracity of an SMS, don’t tap anything in the message.
- Ask a friend: When in doubt, ask a friend or family member to look at the message. They may have insights or be able to identify a scam more easily.
- Enable two-factor authentication: Help protect your accounts by enabling two-factor identification (2FA), wherever it’s available. That way, even if scammers get hold of your access credentials, they’ll have a harder time logging in.
- Don’t reply to the sender: Avoid responding to smishing attempts—even opting out or saying “No” signals your number is active and can trigger subsequent smishing attempts.
- Use data security software: To safeguard your personal information online, use VPNs and other software that minimizes public exposure of your data.
- Update your device: Ensure your phone is updated with the latest software and operating system available to reduce exploitable vulnerabilities.
- Report smishing attacks: Notify your mobile provider if you’re getting a lot of smishing attacks and report scams to the Federal Trade Commission (FTC).
Keep your accounts and your identity safer
People fall for smishing attacks even if they know what to look for. Whether you’ve fallen victim or want to be proactive and get ahead of scammers, identity theft protection services can help keep your identity safer in the future. LifeLock helps you stay on top of the situation by scanning the dark web and monitoring for fraudulent use of your personal data.
And with credit monitoring and fraud alerts†, we’ll help you take swift action to secure your accounts if suspicious activity is detected.
FAQs about text message scams
Want to know more about text message scams? Here are some commonly asked questions about smishing, including what happens if you engage with one and how they differ from phishing attacks.
What is smishing vs. phishing?
Smishing and phishing are both deceptive attacks designed to extract personal information by prompting victims to click links in fraudulent communications or respond with details. The key distinction lies in their delivery methods: phishing typically refers to scam emails, whereas smishing uses SMS text messages to carry out the attack.
What happens if you tap a smishing text link?
Tapping a link in a smishing text can lead to various threats, such as malware being installed on your phone or redirecting you to a fake website that requests your personal information. If you provide sensitive data, hackers can gain access to critical information like your login credentials and passwords, putting your accounts at risk.
What do smishing messages usually want you to do?
The main objective of smishing messages is to entice you to tap a malicious link and either enter your personal information or download malware. More advanced attacks may attempt to trick you into sending a legitimate recovery code from one of your accounts, while simpler smishing scams might just ask you to reply and confirm your email address or date of birth.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.





