Gone are the days when my biggest concern related to financial crime was having my wallet stolen on the packed Metro in Washington, D.C. Now? We also face technology-based crimes, including online identity theft.
In our cyber-focused 21st century, cool digital products and the Internet open a world of easy access to information, entertainment, and other services. But this cyber gateway also presents the possibility of our personal information falling into the wrong hands—and to becoming victims of online identity theft. Even a child's seemingly innocent interactive doll can give our personal information to third parties.
In this article, we’ll share what online identity theft is and how it happens, so you can help protect yourself in our increasingly connected environment.
What Is online identity theft?
Identity theft affects millions of Americans every year and occurs when a fraudster steals your identity—by gaining access to your personally identifiable information (PII)—to commit fraud. While ID theft can happen a number of ways, online ID theft occurs when someone steals your digital PII using scams like planting malicious software on your computer—as opposed to the old, simple technique of, say, stealing your purse.
Your digital PII can include your driver’s license and bank account numbers, as well as any sensitive personal information that can be used to distinguish your identity—and could allow fraudsters to present themselves as you. If a thief gains access to unique personal information like your Social Security number, they can fill out employment forms and even file for a tax refund—all in your name.
How online ID theft happens and what you can do
As we share our personal information online via social media and other digital formats, we may be putting that info at risk of falling into the wrong hands.
Fraudsters use high-tech and other ways to steal digital PII. Knowing what these tactics are may help you protect yourself:
- Phishing occurs when cybercriminals send emails purporting to be from a financial institution or other trusted organization, trying to trick you into opening attachments or clicking on links and providing your PII. Ignore unsolicited emails and online requests for information. If you want to visit, say, your bank’s website to provide information, type in the URL rather than clicking on an emailed link.
- Pharming occurs when your browser, compromised by a virus, is hijacked without your knowledge. You type a legitimate website URL into the address bar, but you’re redirected to a fake site that looks legitimate. There, cybercriminals are able to collect any PII you may type into the website.
- Malicious software. Fraudsters may try to trick you into downloading “malware” that can attack your computer and, possibly, reveal your PII. Consider purchasing online security software for your computer, and keep it—and your computer operating system software—up to date.
- Unsecure websites. Avoid online shopping and other activities on websites that aren’t secure, and be cautious about the apps you use. Make sure you use only official, secure websites with the “https:” prefix—not “http:”.
- Weak passwords used for both social and financial accounts can leave you vulnerable. Strive to use unique, long, and strong passwords for each of your accounts. And when possible, activate multi-factor authentication, which requires you to enter both your log-in credentials and a secret code sent to your smartphone or other device before giving you access to your account.
- Discarded computers and mobile devices that haven’t been wiped of your PII can be another point of access for a thief.
- Targeting children online. Kids can give away personal information online without realizing it. Help protect your children online; be vigilant in monitoring the information they share when using an Internet-connected device.
We’ve all received emails saying we’ve won a too-good-to-be-true prize—redeemed by providing our personal information. As with anything in life, when something online seems too good to be true, it probably is. Don’t respond to emails from someone you don’t know. Don’t click on unknown links or attachments.
The bottom line? You can never be too careful when sharing your personal information online.
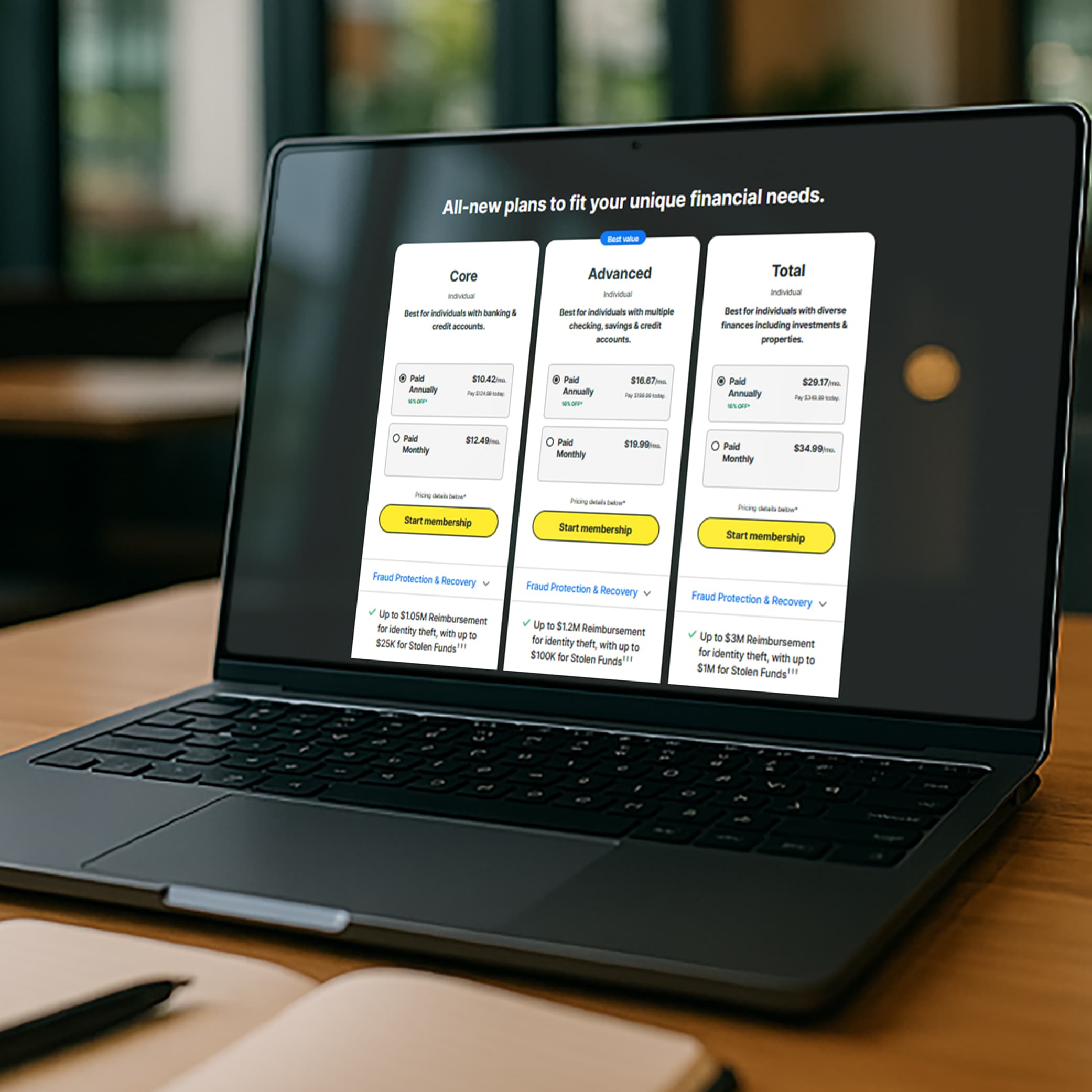
Get LifeLock Identity Theft Protection 30 DAYS FREE*
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.