Cross-site request forgery (CSRF) is a cyber attack that tricks a web application into performing actions on behalf of a user without their knowledge or consent. Also known as session riding, hostile linking, and one-click attacks, CSRF exploits a security flaw where certain web apps fail to properly verify if requests were intentionally initiated.
Imagine you're logged into your banking app in one tab and click an innocent-looking link in another. The link contains a hidden request that secretly triggers a money transfer, exploiting the trust your bank’s website has in your browser.
In that example, the scammer used CSRF to execute a wire transfer scam, but CSRF attacks can be used to perform all sorts of actions, such as changing passwords, making purchases, or posting content on social media against your will.
How does a cross-site request forgery work?
A cross-site request forgery works by exploiting the so-called trusted handshake between a user's browser and a website, allowing an attacker to submit unauthorized requests under the user's credentials. This vulnerability arises if, after a user is authenticated on a site, the site cannot distinguish a forged request from a legitimate one.
Apps and sites have ways of protecting themselves against CSRF attacks, such as requiring re-authentication for important transactions, anti-CSRF tokens, and specific cookie attributes. But if there is no protection against a CSRF attack, hackers can easily impersonate a logged-in user.
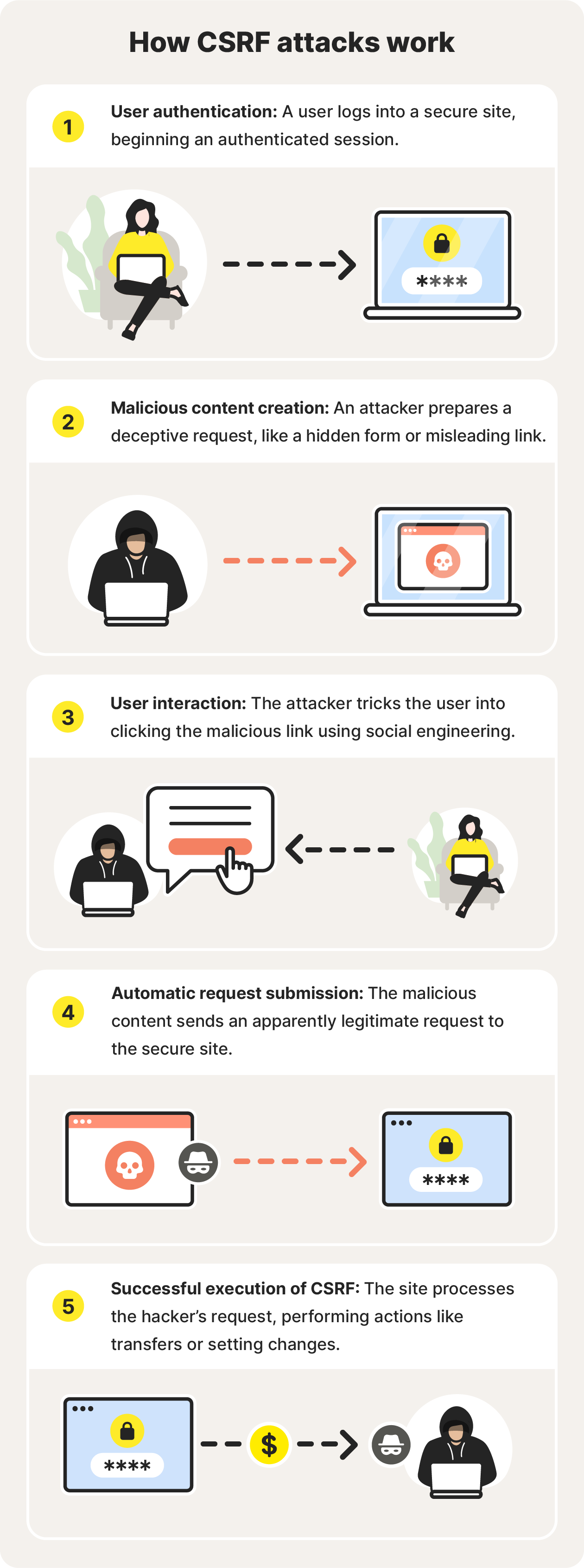
Here’s a step-by-step breakdown of a CSRF attack:
- User authentication: A user logs into a secure website, starting what’s called an authenticated session.
- Malicious content creation: Meanwhile, an attacker has prepared a malicious request, like a deceptive link or hidden form (an invisible part of a webpage that can secretly send data to the server).
- Interaction by user: The attacker persuades the user to click on a link, often manipulating them with social engineering techniques.
- Automatic request submission: The malicious content triggers a request to the secure site where the user is authenticated, making it appear legitimate to the site.
- Successful execution of CSRF: The secure site processes the request as if it were an intentional action by the user, performing tasks like transferring funds, posting content, or changing settings.
Potential consequences and impacts of CSRF attacks
CSRF attacks can have a range of negative consequences for both individuals and businesses. Here is a brief overview of some of these potential impacts:
- Data theft: Individuals are vulnerable to exposure of sensitive personal information and potential identity theft. For businesses, the stakes are even higher, as a major data breach could lead to severe legal repercussions and reputational damage.
- Unauthorized actions: Individuals may suffer financial losses or personal embarrassment due to unauthorized actions performed in their name. In the case of businesses, CSRF attacks can compromise entire web applications, posing a significant threat to corporate integrity and security.
- Financial losses: The risk escalates when CSRF attacks target websites or applications linked to financial services, in which case both individuals and corporations could face substantial monetary losses
Signs of a cross-site request forgery attack
By recognizing the warning signs of a CSRF attack, you’re better equipped to protect your online security and privacy and keep your personal information out of the hands of scammers.
Here are some key CSRF attack signs to watch out for:
- Unexpected or unauthorized actions: Watch out for unexplained changes in your account settings or purchases you didn’t authorize, as these could be signs of identity theft via a CSRF attack.
- Unusual URLs: Strange-looking URLs (for example, with one letter missing in a familiar brand’s name) could be a sign that an attacker is trying to trick you into making an unauthorized request to a different destination.
- Suspicious emails or messages: Receiving confirmation emails or messages related to actions you haven’t performed could indicate somebody is covertly performing actions in your name.
- Strange redirects on websites: Encountering redirects to unfamiliar pages while browsing can be a red flag indicating an attempted CSRF attack.
- Unusual browser behavior: If your browser starts acting up, such as auto-submitting forms or loading pages without your input, it’s a potential sign of a security breach.
- Unusual network activity: Keeping tabs on your network activity using browser developer tools or network monitoring software can shed light on security threats. Unusual patterns or outbound requests to unknown destinations should raise concerns.
- Missing or weak anti-CSRF tokens: Anti-CSRF tokens are unique strings generated by a server to guard against CSRF attacks. They appear in a webpage's HTML source code, and weak or missing tokens can leave a site vulnerable.
What to do if you suspect a CSRF attack
Following best practices for staying safe online can go a long way in protecting you from CSRF attacks, but if you suspect you may have already fallen prey to an attack, here’s what to do:
- Log out immediately: The first step is to log out of the website or application where you suspect the CSRF attack is occurring. This can help prevent further unauthorized actions from being taken on your behalf.
- Clear cookies and cache: Clear your web browser's cookies and cache to remove any potentially malicious scripts or tokens that may have been stored.
- Change passwords: Change your passwords for the affected website or application. Ensure you create strong, unique passwords.
- Report the potential CSRF to website administrators: Notify the administrators or support team of the website or application about your suspicions. They can investigate and take appropriate security measures to help prevent future attacks.
- Scan your device for malware: Run a thorough antivirus and anti-malware scan of your computer or device to check for any malicious software that may have played a role in the attack. Remove any detected threats.
- Enable two-factor authentication (2FA): Use two-factor authentication (2FA) for all the sites and services you use. This can help prevent unauthorized access to your accounts, even if attackers have your login credentials.
Cross-site request forgery examples
Cross-site request forgery attacks can target a wide range of online activities. For example, in 2020, the TikTok Careers portal was found to have a vulnerability related to the platform’s use of single sign-on with Facebook or LinkedIn that could have allowed hackers to take over user accounts with a single click. TikTok quickly resolved the issue, but it shows how even popular and trusted apps can be vulnerable.
A similar bug was identified in the early days of YouTube. In 2008, Princeton researchers discovered a vulnerability that allowed hackers to perform nearly all the same actions as a logged-in user, including sending messages to and sharing videos with contacts, flagging inappropriate content, and adding videos to favorites.
Even online security software companies are not immune. In 2014, researchers found multiple CSRF vulnerabilities in the User Management module of McAfee’s Network Security Manager—an enterprise-level cybersecurity product. The vulnerability was quickly patched, but the example demonstrates how serious a CSRF threat can be.
Preventing CSRF attacks
CSRF attacks are sophisticated, and, by their very nature, extremely difficult to guard against. But there are several simple actions you can perform to help protect against a CSRF attack:
- Log out of your accounts when you’re not using them: A CSRF attack relies on an authenticated session, so logging out of all accounts once you’re finished reduces your exposure to these kinds of attacks.
- Use browser extensions: Certain browser extensions or add-ons can provide anti-CSRF protection by monitoring and blocking suspicious activities such as unauthorized requests from websites.
- Regularly clear cookies and cache: Regularly clearing your browser’s cookies and cache removes malicious scripts or tokens that might have been stored on your device during a browsing session.
- Use a password manager: A reputable password manager can generate strong, unique passwords for you while also storing them so you don’t have to worry about remembering them yourself.
- Be cautious with emails and links: CSRF attacks usually rely on malicious phishing links or email attachments—always be cautious with links and emails from unknown or suspicious sources.
Protect yourself from CSRF attacks
When it comes to fighting off CSRF attacks and other advanced online privacy threats, expert support is critical.
LifeLock offers industry-leading identity theft protection, with a broad range of specialized features including dark web monitoring that scans for your personal information, and dedicated assistance from U.S.-based Restoration Specialists to help you manage the consequences should you become a victim of identity theft. Join millions of others who rely on LifeLock for greater peace of mind.
FAQs about cross-site request forgery attacks
Read on for answers to some common questions about CSRF attacks.
How do you protect against cross-site request forgery attacks?
The best protection involves a mix of diligent security habits and reliable cybersecurity tools. Always log out of websites and apps when you’re done, be wary of clicking suspicious links or opening unknown emails, and use trusted cybersecurity software for an extra layer of security.
Is there a difference between XSS vs CSRF?
Yes, XSS and CSRF are two different types of attacks. XSS stands for Cross-Site Scripting and is a cyber attack that exploits vulnerabilities in a website to inject malicious scripts, whereas CSRF tricks users into executing unsafe actions on a website where they are currently authenticated.
Why is a CSRF token required?
A CSRF token is a unique, secret, and unpredictable string of characters—a bit like a password—that’s generated by the website’s backend and transmitted to the user’s web browser. It ensures that requests sent to the server are legitimate and coming from the authenticated user.
How common are CSRF attacks?
Due to increased awareness and improved security practices, CSRF attacks are less common today than they used to be. However, they remain a concern, especially on websites that handle sensitive information or transactions.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. For more details about how we create, review, and update content, please see our Editorial Policy.
This article contains
- How does a cross-site request forgery work?
- Potential consequences and impacts of CSRF attacks
- Signs of a cross-site request forgery attack
- What to do if you suspect a CSRF attack
- Cross-site request forgery examples
- Preventing CSRF attacks
- Protect yourself from CSRF attacks
- FAQs about cross-site request forgery attacks
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.




-and-prevention-tips-thumb.jpg)